LockBit Ransomware Recovery and Decryption
Has LockBit ransomware encrypted your data? If so, it may be an emergency, but it’s important to stay calm. Learn more about the Lockbit ransomware, decryption, recovery, removal and statistics. You can also contact our awesome emergency response team of cybersecurity ransomware data recovery experts 24/7 and get a FREE and immediate assessment of the damages.
We handle cases for all sizes of organizations, worldwide. All operations are managed remotely by our team of highly specialized technicians. We can help you in recovering your data through a fast and efficient ransomware removal and remediation process.

What should I do if and when my data has been encrypted by Lockbit?
- Disconnect your system from the network immediately. For more details, please visit our contact us.
- It is better NOT to talk with the attackers, as they are skilled at taking advantage of inexperienced negotiators.
- Report the crime to the relevant law enforcement authorities.
- Ensure that the affected machine is shut down. If left on its own, Lockbit may continue encrypting your data in the background.
- Talk to the experts. Get HELP now!
lockbitdecryptor is a licensed and registered Cyber Security firm and we’re here to help you with Lockbit ransomware removal. We have lots of experience in this field, so we know how difficult this situation is. Thanks to our expertise and knowledge, we can recover 100% of your encrypted data in the vast majority of cases.
Lockbit uses military grade encryption technology to hold your organization hostage. Any attempts at recovering the data with a quick fix are unlikely to work. lockbitdecryptor is Europe’s leading ransomware recovery firm, and we can help you get back online as quickly as possible.
Keep calm! Contact us now for a consultation and learn about your options!
LOCKBIT RANSOMWARE STATISTICS & FACTS
The groups that operate Lockbit ransomware are known for targeting large organizations. The gang is known to customize ransom demands based on the annual revenue of their victims.
The average Lockbit ransom amount is somewhere around $33,000. Ransoms are usually paid in Bitcoin. Most quick-buy methods of purchasing Bitcoin via methods like PayPal or credit card will also apply a fee of up to 10%.
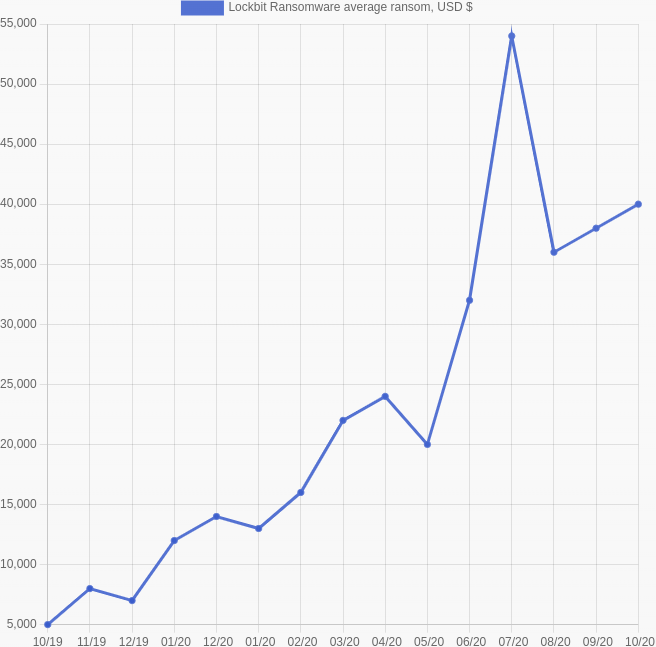
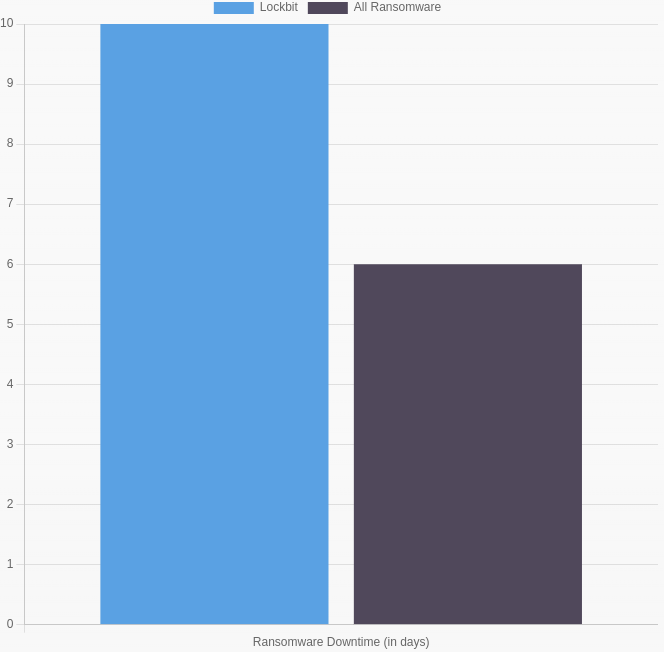
Downtime resulting from Lockbit ransomware is often longer than with normal ransomware attacks. The manual process of communicating with the attackers can further delay response time.
For many organizations, downtime is the most expensive part of a ransomware incident. Another negative side effect of a data breach can be damage to your reputation.
Your goal should be to get your systems back to a productive state as soon as possible. The best way to do this is to call in experts who know the ins and outs of Lockbit ransomware to complete the removal and restoration process immediately.
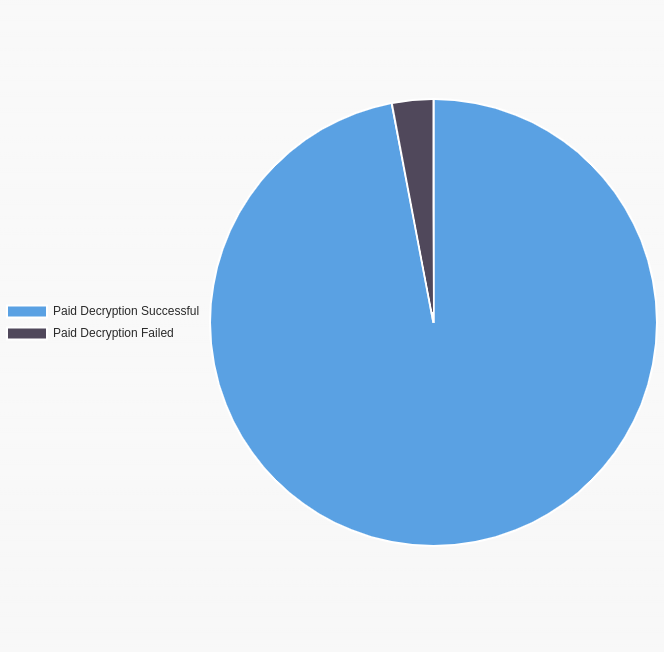
In our experience, a successful ransom payment usually results in getting a working Lockbit decryptor. Decryptor tools do take work to maintain, however, so not all attackers have working tools.
It’s important to know which gang you are dealing with. Some attackers are careful to maintain a good reputation, and always provide working Lockbit decryptors. Others are known to be scammers, and will never provide a decryptor after receiving payment.
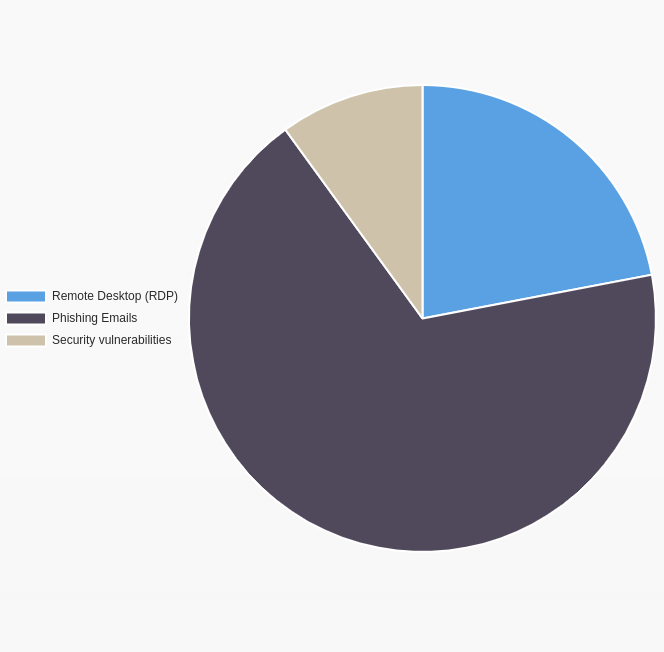
The most common attack vector for Lockbit ransomware is phishing.
| LOCKBIT RANSOMWARE SUMMARY | |
|---|---|
| Name | Lockbit Virus / Lockbit Ransomware |
| Danger level | Very High. Advanced Ransomware which makes system changes and encrypts files |
| Release date | 2019 |
| OS affected | Windows, Vmware esxi server, Mac, Linux |
| Appended file extensions | .HLJkNskOq .lockbit .fxkJts2wg |
| Ransom note | “Restore-my-files.txt” |
| Known scammers | none |
What is Lockbit 3.0 Ransomware?
LockBit 3.0 ransomware has emerged as a significant cybersecurity threat, causing havoc among businesses worldwide. This article aims to delve into the workings of LockBit 3.0, its impact, prevention strategies, and steps to recover from an attack.
What is LockBit 3.0 Ransomware? LockBit 3.0 is a sophisticated form of malware designed to encrypt a victim’s files and demand a ransom for decryption. This strain has evolved from its predecessors, featuring enhanced encryption algorithms and stealthier infiltration methods.
Key Features and Modus Operandi:
- Encryption: LockBit 3.0 employs advanced encryption algorithms like RSA and AES to lock victims’ files, making them inaccessible.
- Ransom Note: After encryption, it generates a ransom note demanding payment (usually in cryptocurrencies) in exchange for a decryption key.
- Network Disruption: This ransomware can infiltrate entire networks, causing widespread data encryption and operational disruption.
Targets and Impact: LockBit 3.0 predominantly targets organizations, aiming to maximize ransom payouts. It has impacted various sectors, including healthcare, finance, and government, causing financial losses and reputational damage.
Preventive Measures Against LockBit 3.0:
- Updated Security Software: Regularly update antivirus and anti-malware software to detect and prevent ransomware attacks.
- Employee Training: Educate staff about phishing emails, suspicious links, and the importance of strong passwords to mitigate the risk of infiltration.
- Data Backup: Maintain secure and updated backups to restore files without succumbing to ransom demands.
- Network Segmentation: Segmenting networks limits the spread of ransomware, minimizing potential damage.
Recovery from LockBit 3.0 Ransomware Attack:
- Isolation: Immediately isolate infected systems to prevent further encryption and damage.
- Professional Assistance: Seek help from cybersecurity experts to assess the extent of the attack and identify possible recovery options.
- Decryptor Tools: Explore available decryptor tools released by security firms to unlock files without paying the ransom.
- Data Restoration: Restore data from secure backups to resume operations.
Special Note:
“If you lack backups or find that other free tools aren’t effective, reach out to us via WhatsApp for assistance with comprehensive LockBit 3.0 Ransomware decryption. We offer affordable rates and ensure a 100% recovery guarantee.”
HOW TO IDENTIFY LOCKBIT RANSOMWARE
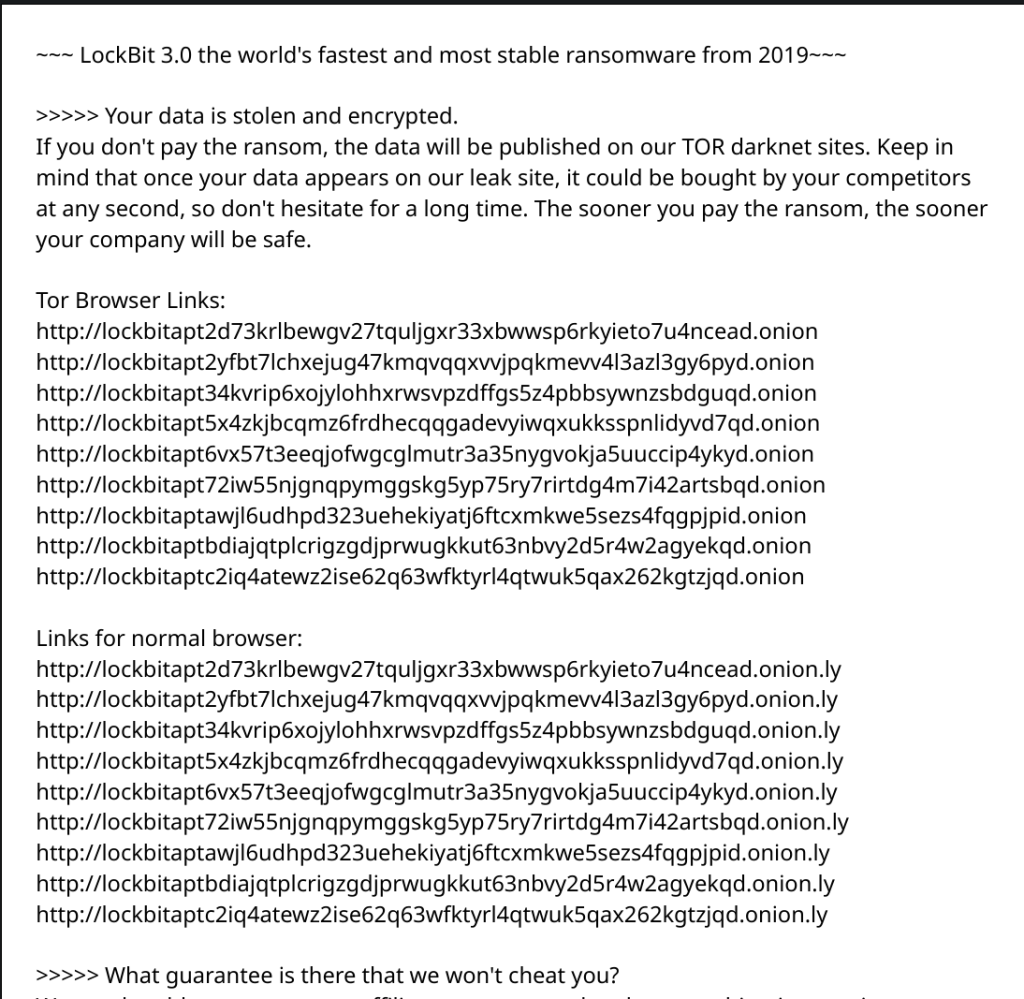
There is almost always a .txt file in every encrypted folder. The text file usually has the name “Restore-My-Files.txt” and contains all the necessary information to contact the Lockbit Ransomware attackers to try and get your data back.
It’s usually safe to open this file, just be sure the file extension is .txt. At this stage, the main risk you face is that the attackers will use scare tactics or threats to try to extort more money.
Another common tactic is demanding double or triple payments. In our experience, the use of professional negotiators consistently results in lower payments. Having experts handle negotiation, decryption, and improving security after the incident is the best option for most organizations.
Lockbit Ransomware Note #1: .txt Notice
Lockbit 3.0 For Esxi Servers
LockBit 3.0, a notorious strain of ransomware, poses significant threats to ESXi environments. This article aims to delve into the specific risks associated with LockBit 3.0 targeting ESXi, protective measures to safeguard your virtualized infrastructure, and recovery strategies in case of an attack.
What is LockBit 3.0 for ESXi?
LockBit 3.0 tailored for ESXi is a malicious software designed to target VMware’s ESXi hypervisor, encrypting crucial data and rendering virtual environments inaccessible. This version is adapted to infiltrate ESXi servers, affecting entire virtualized infrastructures.
Key Features and Modus Operandi:
- ESXi Targeting: LockBit 3.0 for ESXi specifically targets VMware’s ESXi hypervisor, exploiting vulnerabilities to gain access and encrypt virtual machines and their associated files.
- Encryption: It utilizes advanced encryption methods, often RSA or AES algorithms, to lock ESXi-hosted virtual machines, rendering them unusable until a ransom is paid.
- Extortion: Following encryption, the attackers demand a ransom in cryptocurrencies, threatening to delete the decryption keys if payment isn’t made within a specified timeframe.
Risks and Impact on ESXi Environments: LockBit 3.0’s attack on ESXi environments can paralyze critical operations within organizations relying on virtualized infrastructures. The impact extends beyond individual machines, potentially disrupting entire networks and services, causing severe financial losses and operational downtime.
Protection Strategies for ESXi Against LockBit 3.0:
- Regular Updates and Patches: Keep ESXi hypervisors and associated software updated with the latest security patches to close known vulnerabilities.
- Strong Access Controls: Implement robust access controls and authentication mechanisms to prevent unauthorized access to ESXi environments.
- Network Segmentation: Segment networks hosting ESXi servers to contain and limit the spread of any potential ransomware attack.
- Backup and Disaster Recovery: Maintain regular, encrypted backups of ESXi virtual machines and associated data in separate, secure locations.
Recovering from LockBit 3.0 Attack on ESXi:
- Isolation: Immediately isolate affected ESXi servers to prevent further encryption and damage to other virtual machines.
- Professional Assistance: Engage cybersecurity experts to assess the extent of the attack and identify recovery options, including potential decryption tools or techniques.
- Restoration from Backups: Utilize secure backups to restore encrypted virtual machines and data, ensuring minimal data loss and business continuity.
Conclusion: LockBit 3.0 targeting ESXi environments poses a grave threat to the stability and security of virtualized infrastructures. Implementing stringent security measures, regular backups, and a well-defined recovery plan are essential in mitigating and recovering from such ransomware attacks.
Lockbit 3.0 for Windows Servers
Understanding LockBit 3.0 for Windows Servers: LockBit 3.0 is a variant of ransomware that specializes in infiltrating Windows-based servers. It employs sophisticated techniques to encrypt critical data stored on these servers, holding it hostage until a ransom is paid.
Key Features and Modus Operandi:
- Targeting Windows Servers: LockBit 3.0 specifically focuses on exploiting vulnerabilities in Windows server environments, aiming to encrypt sensitive files and databases.
- Encryption: Utilizing potent encryption algorithms such as AES and RSA, it encrypts server data, rendering it inaccessible without the decryption key.
- Ransom Demand: Once the encryption process is complete, it prompts victims to pay a ransom, typically in cryptocurrencies, in exchange for the decryption key.
Risks and Impact on Windows Servers: LockBit 3.0’s attack on Windows servers can have dire consequences, causing significant disruption to business operations. The potential loss of critical data and operational downtime can lead to severe financial ramifications and reputational damage.
Protective Measures for Windows Servers Against LockBit 3.0:
- Regular Patching: Ensure Windows servers are regularly updated with the latest security patches to mitigate known vulnerabilities.
- Endpoint Security: Employ robust endpoint security solutions to detect and prevent ransomware attacks targeting servers.
- Access Control and Monitoring: Implement stringent access controls and monitor server activities to detect suspicious behavior promptly.
- Data Backups: Maintain regular, encrypted backups of critical server data stored in secure, off-site locations to facilitate restoration without succumbing to ransom demands.
Recovery Strategies from LockBit 3.0 Attack on Windows Servers:
- Isolation: Immediately isolate infected servers to prevent further encryption and limit the spread of the ransomware across the network.
- Expert Assistance: Engage cybersecurity professionals to assess the impact and explore potential decryption methods or tools.
- Restoration from Backups: Utilize secure backups to restore encrypted server data, enabling the recovery of affected systems while minimizing data loss and operational downtime.
Conclusion: LockBit 3.0’s focus on targeting Windows servers underscores the critical need for robust security measures and preparedness against evolving ransomware threats. Proactive defense, regular updates, backups, and a well-defined recovery strategy are imperative to safeguarding Windows server environments.
How Does Lockbit 3.0 Attack on Windows, Esxi and RDPs?
LockBit 3.0, a sophisticated strain of ransomware, employs various tactics to infiltrate and compromise different systems like Windows, ESXi, and RDP connections.
- Windows Systems:
- Exploiting Vulnerabilities: LockBit 3.0 targets vulnerabilities in Windows operating systems, often exploiting security loopholes or weaknesses in software and services. It might use methods like phishing emails with malicious attachments or links, software vulnerabilities, or brute force attacks against weak passwords to gain access to Windows systems.
- Advanced Encryption: Once it infiltrates a Windows system, LockBit 3.0 uses advanced encryption algorithms like AES or RSA to encrypt files, making them inaccessible to users. This encryption process is often swift and thorough, affecting critical files and system resources.
- ESXi (VMware):
- Exploiting ESXi Vulnerabilities: LockBit 3.0 specifically targets vulnerabilities within VMware’s ESXi hypervisor. It might exploit security weaknesses in ESXi, potentially gaining access through vulnerabilities in outdated software versions, misconfigurations, or exposed services.
- Encrypted VMs: Upon compromising the ESXi server, LockBit 3.0 encrypts virtual machines (VMs) hosted on the ESXi infrastructure. This encryption directly impacts the functionality of these VMs, rendering them unusable until the ransom is paid or recovery methods are applied.
- Remote Desktop Protocol (RDP):
- Exploiting RDP Weaknesses: LockBit 3.0 takes advantage of weaknesses in RDP, a protocol used for remote access to Windows systems. It might target systems with exposed RDP ports, weak or default passwords, or unpatched RDP vulnerabilities.
- Encryption of Accessible Data: Once access is gained through compromised RDP connections, LockBit 3.0 encrypts files and data accessible via these connections. This could include critical business data, documents, or system resources, causing disruptions and data loss.
In all cases, LockBit 3.0 aims to encrypt sensitive data within these systems or infrastructures and demands a ransom in exchange for a decryption key. The methods of attack might vary slightly depending on the specific vulnerabilities or weaknesses it can exploit in each system, but the primary goal remains consistent: to encrypt data and extort victims for financial gain.