How to Unlock .Encrypt3 Files and Decrypt Mimic/Pay2Key Ransomware?
Advanced .Encrypt3 Decryptor by Experts
Mimic, also known as Pay2Key, is one of the latest ransomware families that has disrupted businesses by encrypting files with the .Encrypt3 extension. Our cybersecurity team has developed a specialized decryptor that restores .Encrypt3-locked data without depending on the attackers. It has been tested in enterprise environments, including Windows Server and VMware infrastructures, ensuring reliable recovery.
Related article: How to Decrypt Bruk Ransomware (.bruk) and Recover Encrypted Files?
Inside Look at the Mimic/Pay2Key Encryption
The ransomware targets critical files such as databases, executables, and images. Once executed, it attaches the .Encrypt3 extension to all affected files, leaving them inaccessible. A ransom note is created that includes a unique decryption ID and contact instructions. Victims are often asked to email the operators at addresses like dataleaks5@gmail.com.
Mimic follows the trend of other advanced ransomware groups by combining file encryption with data theft, making recovery difficult without professional support.
Also read: How to Remove LockSprut Ransomware and Restore (.rupy3xz1) Encrypted Files?
How Our .Encrypt3 Decryptor Operates?
Our decryptor was built through reverse engineering of Mimic/Pay2Key samples and is continuously updated as new variants emerge. It functions in a controlled environment to guarantee data integrity and safety.
- Decryption ID Mapping – Extracts the identifier from ransom notes to align with encryption batches.
- Secure Scan Mode – Identifies encrypted files and ensures no corruption before decryption begins.
- Blockchain-Verified Recovery – Uses blockchain-backed verification to confirm file integrity after recovery.
- Universal Key Mode – Provides optional support when the ransom note is missing or partially corrupted.
Prerequisites for Running the Tool
To initiate successful recovery, the following items are needed:
- The ransom note (commonly saved as ILETISIM.txt)
- Access to at least one encrypted sample file with the .Encrypt3 extension
- Stable internet connection for cloud-based processing
- Administrator privileges for scanning and execution
Immediate Response After a .Encrypt3 Attack
When a system is compromised by Mimic ransomware, quick and careful response is critical.
- Disconnect from the Network – Isolate infected devices immediately.
- Do Not Delete Evidence – Keep ransom notes, encrypted files, and logs intact for forensic analysis.
- Preserve Backups and Snapshots – Verify whether backups remain untouched and avoid overwriting them.
- Avoid Attacker Communication – Do not send files to attacker emails, as this risks additional compromise.
- Seek Professional Guidance – Work with experts to analyze the infection and evaluate recovery options.
Decrypting Mimic/Pay2Key and Restoring Operations
The Mimic/Pay2Key ransomware is notorious for precision attacks on servers and enterprise networks. While no official free decryptor currently exists, victims can explore recovery through a mixture of free and paid solutions. The effectiveness of these methods varies based on the infection stage and system defenses.
Recovery Paths for .Encrypt3 Files
Free Methods Available
Backup Recovery
The most reliable method is restoring data from clean, offline backups. This works if the attackers have not deleted or encrypted them. Administrators must validate backup integrity before using them.
Virtual Machine Snapshots
For organizations running virtualized infrastructures, pre-infection VM snapshots offer a quick rollback solution. However, if attackers accessed hypervisors, these snapshots may be damaged or deleted.
Security Community Tools
Platforms like ID Ransomware, NoMoreRansom, and MalwareBazaar can assist in identifying variants and providing initial analysis.
Paid Recovery Options
Ransom Payment
Attackers provide a decryptor after payment. However, this carries major risks: incomplete decryption, hidden malware in the decryptor, or no response after payment. Law enforcement also discourages this due to funding criminal operations.
Negotiation Services
Third-party negotiators may engage with the attackers on behalf of the victim. They aim to lower ransom costs and confirm that decryption tools are functional. This method is costly and does not guarantee success.
Our Advanced .Encrypt3 Decryptor
We offer a professional-grade decryptor specifically designed for Mimic/Pay2Key ransomware. Unlike attacker-provided tools, it ensures safe recovery in a sandboxed environment with data integrity checks. Our solution supports both offline and online recovery, making it versatile for enterprise-scale incidents.
How to Use Our Mimic/Pay2Key (.Encrypt3) Decryptor
Our decryptor is built with enterprise-grade reliability and precision. It leverages the unique victim identifier found inside the ransom note (example: Yuru-OERMzNpTYffk0xdXUp7xgu7JBbMnxnLErVMv9LYH8hc*Encrypt3) to map encrypted files to their respective decryption keys.
Step 1: Gather Requirements
Before running the decryptor, ensure you have:
- A copy of the ransom note (ILETISIM.txt)
- At least one encrypted file (e.g., database.mdf.Encrypt3)
- Administrative privileges on the system
- An active internet connection for secure decryption processing
Step 2: Initial Setup
- Download and install the decryptor package provided by our recovery team.
- Run the decryptor in administrator mode to ensure access to protected directories.
- Upload the ransom note and one encrypted file for validation.
Step 3: Victim ID Matching
- The decryptor will extract your unique identifier from the ransom note.
- This identifier will be used to match your encrypted batch with our cloud-based decryption infrastructure.
Step 4: Safe File Assessment
- The tool will scan encrypted files in read-only mode to confirm status and compatibility.
- A small set of test files will be decrypted first to validate integrity.
Step 5: Begin Full Decryption
- Once the test passes, launch the full decryption process.
- Files will be restored to their original directories with their original extensions.
- Progress is logged and available for audit purposes.
Step 6: Verification and Post-Recovery
- After decryption, the tool generates an audit report including file hashes for verification.
- System hardening recommendations will be provided to prevent reinfection.
Also read: How to Decrypt (.DarkRuss_CyberVolk) Files Locked by DarkNetRuss Ransomware?
Technical Profile of Mimic/Pay2Key
The ransomware has been linked to threat groups with ties to advanced persistent threats. Its operation blends stealth and aggression, ensuring maximum impact on victims.
Tools and Techniques Used by Attackers
Mimic/Pay2Key operators deploy a wide range of legitimate and malicious tools to compromise environments.
- Initial Access: Brute-force attacks against RDP, VPN vulnerabilities, and phishing campaigns.
- Credential Harvesting: Tools like Mimikatz and LaZagne to steal stored passwords.
- Network Reconnaissance: Advanced IP Scanner and SoftPerfect Scanner used to map networks.
- Privilege Escalation: Exploitation of misconfigured Active Directory services.
- Data Exfiltration: Utilities like RClone, FileZilla, and WinSCP to upload data to external servers.
- Defense Evasion: Abuse of legitimate software like Zemana and PowerTool to bypass detection.
- Encryption Stage: A hybrid encryption approach combining fast symmetric encryption with strong asymmetric key protection.
- Cleanup: Deletion of shadow copies with vssadmin commands to disable easy recovery.
Known Indicators of Compromise (IOCs)
- File Extension: .Encrypt3 appended to encrypted files (e.g., document.jpg.Encrypt3).
- Ransom Note Name: ILETISIM.txt.
- Attacker Email: dataleaks5@gmail.com.
- Decryption ID Format: Random alphanumeric string followed by *Encrypt3.
- Hash Example: d1e3668635a3c594e9315eae78d23925533dbe1a (sample shared by a victim).
Global Impact and Victim Statistics
Mimic/Pay2Key has been reported across multiple sectors, from manufacturing to government agencies. It often targets critical infrastructure where downtime has devastating consequences.
Countries Most Impacted
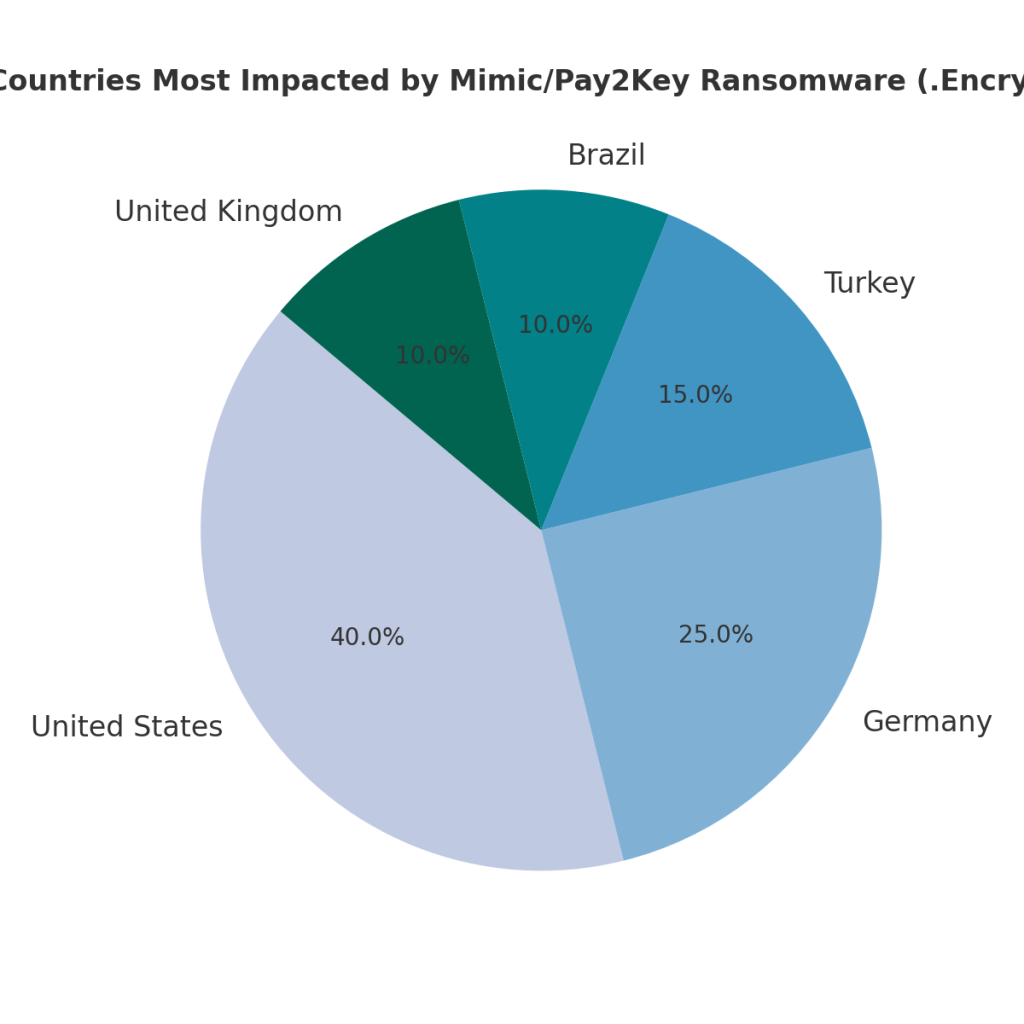
Industries Affected
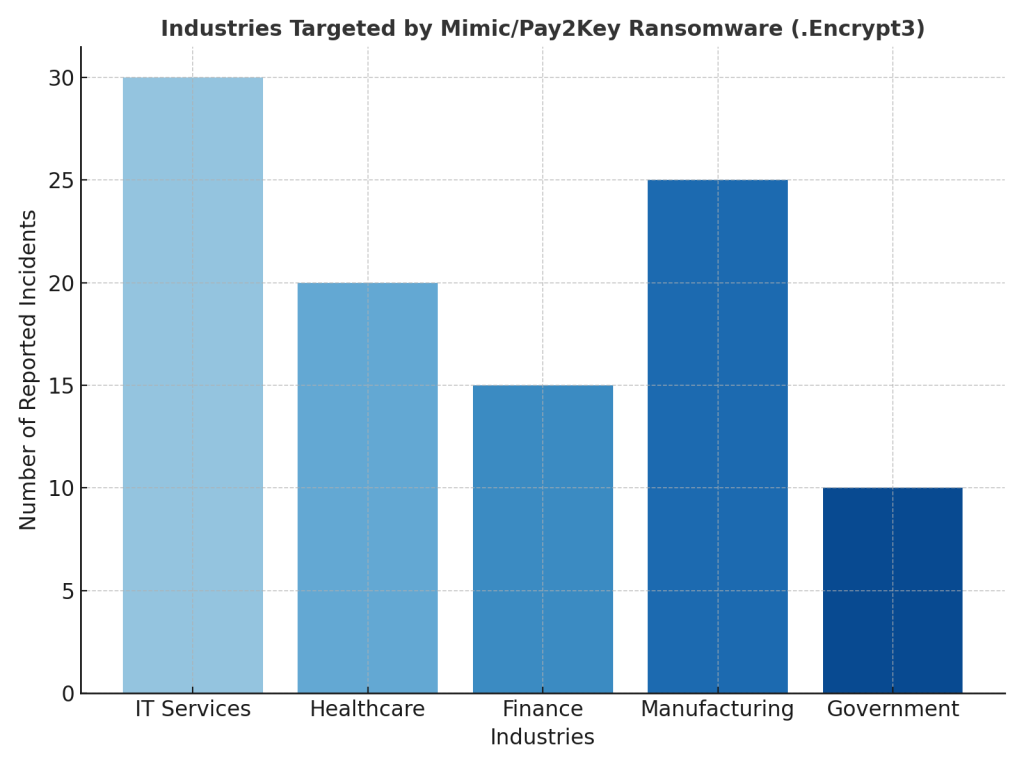
Timeline of Attacks
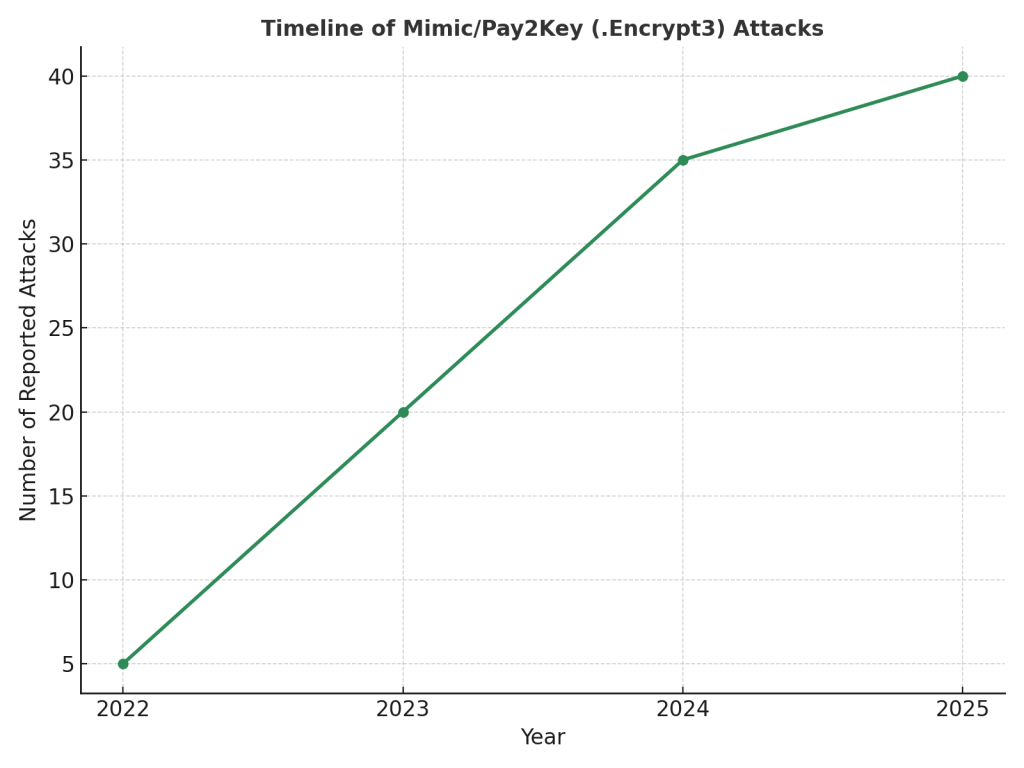
Final Thoughts: Regaining Control After a .Encrypt3 Attack
Being hit by Mimic/Pay2Key ransomware with the .Encrypt3 extension can be overwhelming. Quick isolation, forensic preservation, and professional response are critical to recovery. While free methods exist, they may not work for newer Mimic variants. Paid options, particularly professional decryptor services, provide the best chance of regaining access to encrypted data without supporting cybercriminals.
Frequently Asked Questions
Contact Us To Purchase The .Encrypt3 Decryptor Tool







3 Comments