How to Decrypt .phenol Files after Phenol Ransomware Attack?
Introduction: Understanding Phenol Ransomware
Phenol ransomware is a file-encrypting malware strain that appends the .phenol extension and demands a hefty ransom from victims. Once it infects a system, it locks critical files and creates a ransom note titled Encrypt.html, instructing victims to contact the attackers via email.
This variant is particularly destructive, combining strong cryptography with data exfiltration tactics. Victims not only face data encryption but also the risk of sensitive information being leaked if they fail to comply with demands.
Related article: How to Decrypt Lamia Loader (.enc.LamiaLoader) Ransomware Files?
How the Phenol Ransomware Encryption Works?
Phenol uses robust cryptographic algorithms to lock files, making them inaccessible without a unique decryption key. For example, a file named photo.jpg becomes photo.jpg.[Hulk67888@outlook.com].phenol. The ransom note warns users not to terminate processes or attempt manual decryption, claiming it will result in permanent data loss.
The encryption process is fast and recursive, spreading across local drives, connected storage devices, and sometimes network shares, leading to widespread damage.
Also read: How to remove Theft Ransomware (.theft) and Recover Data?
Immediate Response After a Phenol Attack
The first few minutes after a ransomware attack are crucial. Victims should take these steps to minimize damage and preserve evidence.
Isolate the System
Disconnect infected machines from the network to prevent further file encryption and lateral spread.
Preserve Critical Evidence
Do not delete ransom notes or encrypted files. Keep network traffic logs, file hashes, and timestamps intact for forensic analysis.
Avoid Reboots or Wipes
Rebooting the system may trigger additional encryption routines. Similarly, wiping data can destroy recovery opportunities.
Contact Experts
Rely on cybersecurity professionals instead of unverified tools or shady online guides. Early professional intervention drastically improves recovery success rates.
Phenol Ransomware File Decryption and Recovery Paths
Free Recovery Methods
Security Vendor Tools
At present, no universal decryptor is available for Phenol. Some security vendors may provide partial decryptors for earlier flawed variants, but they are ineffective against current builds. Victims should verify the legitimacy of free tools to avoid data corruption.
Backup Restoration
If offline or off-site backups exist, organizations can restore them to resume operations. However, backups must be verified for integrity before use, since some may have been partially encrypted or infected.
Virtual Machine Snapshots
If infrastructure relies on VMware or similar hypervisors, reverting to pre-attack snapshots can restore functionality. Snapshots should be verified for deletion attempts, as ransomware operators often try to corrupt or remove them.
Paid Recovery Methods
Paying the Ransom
Attackers demand $5000 in Tether (USDT), promising a decryptor tied to the victim’s login ID. However, compliance carries major risks—attackers may provide a faulty tool, corrupt files, or withhold decryption keys altogether. Legal and ethical implications also make this route highly discouraged.
Negotiation Services
Some third-party negotiators mediate with attackers, attempting to reduce ransom demands and secure proof-of-decryption before payments. While this may improve success rates, costs are often high and outcomes uncertain.
Our Phenol Ransomware Decryptor
Our expert-built Phenol Decryptor is a professional-grade tool engineered to safely recover files encrypted by Phenol ransomware.
- Reverse-Engineered Core – Built from deep analysis of Phenol’s cryptographic flaws and decryption structures.
- Cloud-Assisted Recovery – Secure sandbox environments verify data before decryption, ensuring accuracy.
- Login ID Integration – Uses ransom note IDs for precise key-matching.
- Offline & Online Options – Works in air-gapped environments or through secure encrypted transfers.
This solution has successfully restored data for multiple organizations without requiring ransom payments.
Also read: How to Decrypt Bitco1n (.Bitco1n) Ransomware Files?
Technical Insights: Phenol Attack Vectors
Initial Entry Points
Phenol commonly infiltrates through phishing campaigns, malicious attachments, cracked software downloads, or vulnerabilities in outdated systems. Drive-by downloads and compromised websites also play a role.
Tools and TTPs Used by Operators
Phenol campaigns align with several MITRE ATT&CK tactics:
- Credential Harvesting – Tools like LaZagne and Mimikatz are used to extract credentials from browsers and memory.
- Network Scanning – Utilities like Advanced IP Scanner help attackers map internal networks.
- Defense Evasion – Obfuscation tools and rootkits allow malware to bypass antivirus detection.
- Exfiltration – Programs such as RClone, FileZilla, and Mega.nz clients are used to transfer stolen files.
- Encryption Process – Phenol leverages asymmetric cryptography, deleting shadow copies with commands such as vssadmin delete shadows.
Indicators of Compromise (IOCs) for Phenol
Victims can identify infections using the following markers:
- File Extensions – Encrypted files include .phenol appended with attacker email.
- Ransom Note – Encrypt.html appears in affected directories.
- Contact Address – Attackers use Hulk67888@outlook.com.
- Detection Names – Examples include Ransom.Phenol (Malwarebytes) and Trojan-Ransom.Win32.Crypmodng.btr (Kaspersky).
- Suspicious Tools – AnyDesk, RClone, or Ngrok may appear post-compromise.
Geographic and Sectoral Impact of Phenol
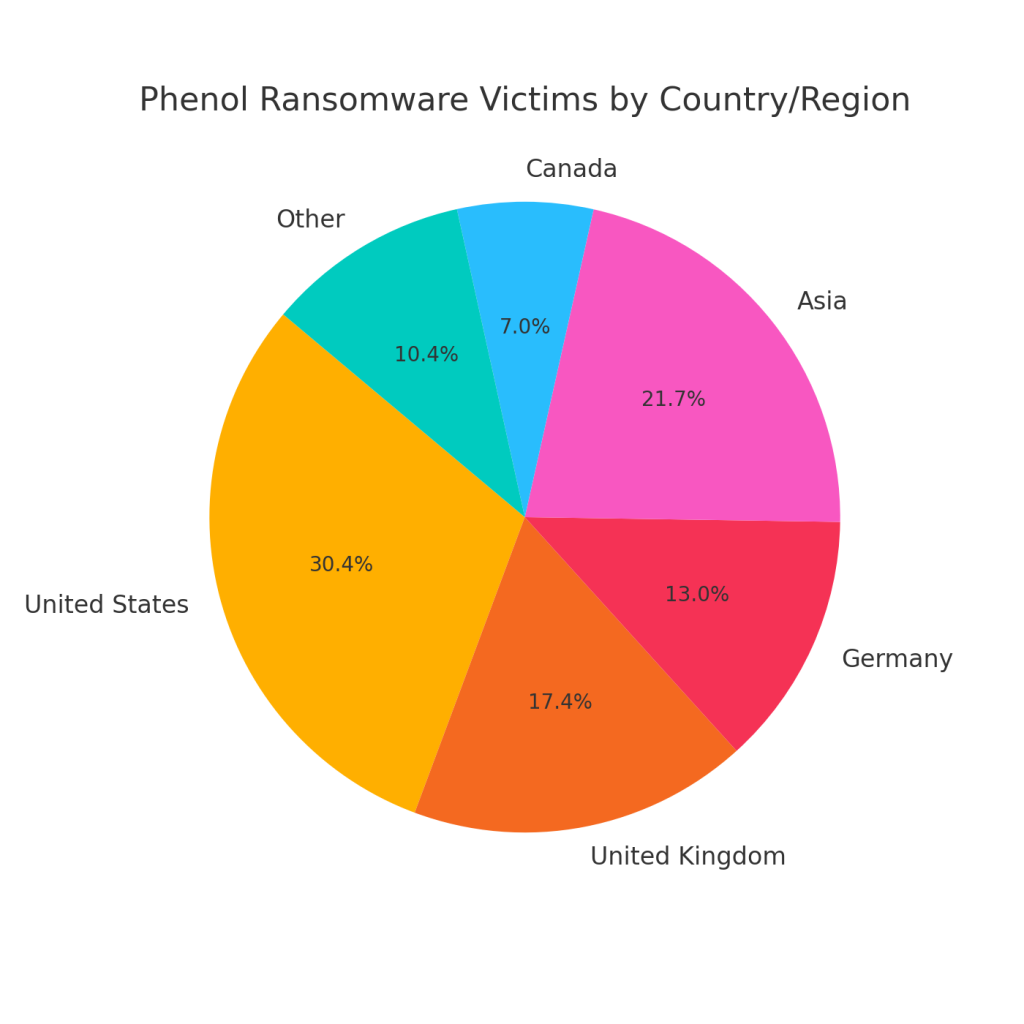
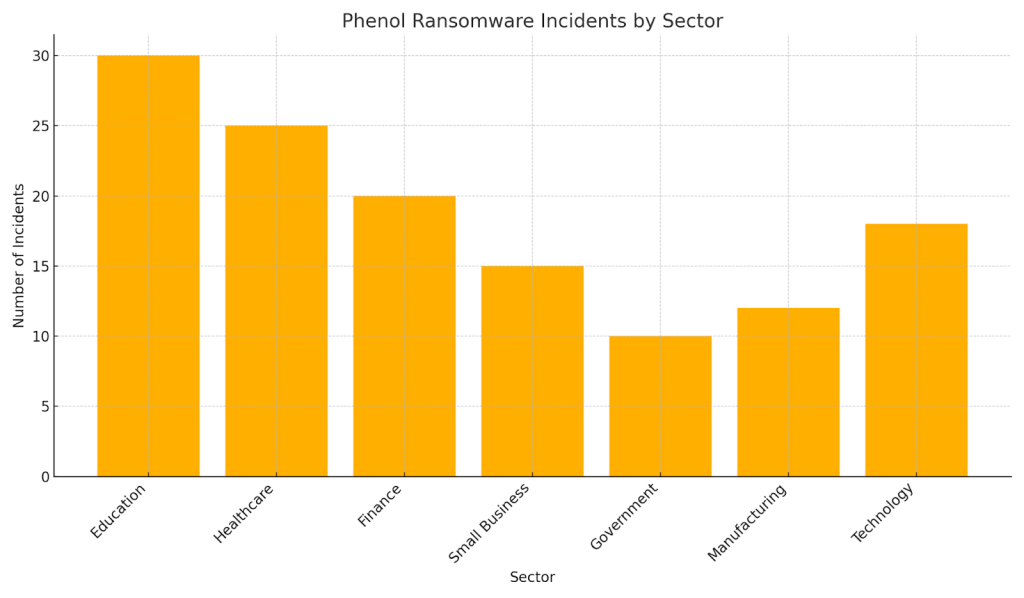
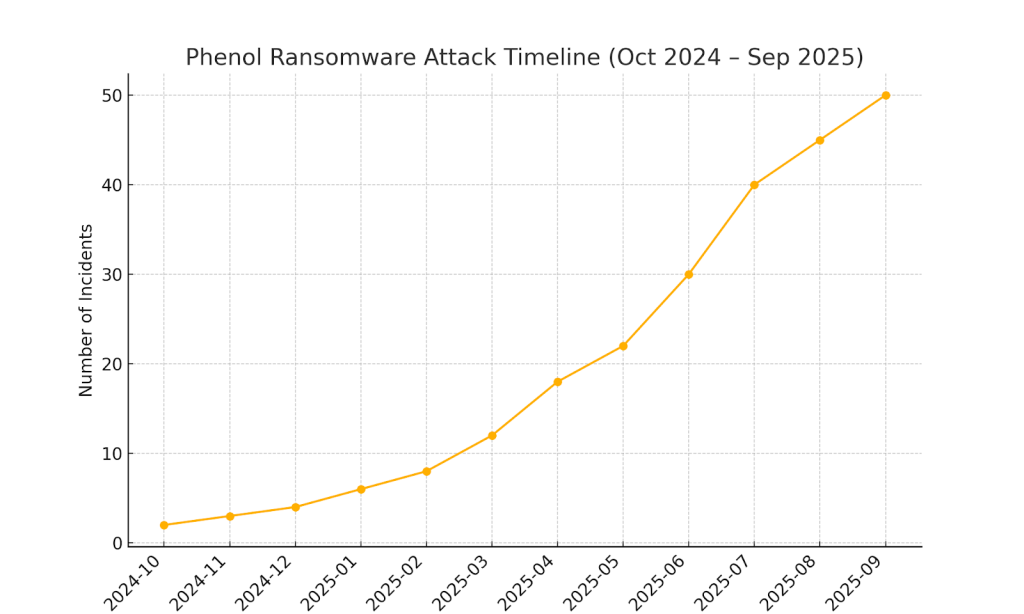
Phenol has targeted a mix of businesses and individual users, with early reports linking it to campaigns in North America, Europe, and parts of Asia. Its double-extortion model makes it attractive for targeting both small enterprises and larger institutions.
Countries Affected by Phenol
Organizations Hit by Phenol
Timeline of Attacks
Dissecting the Phenol Ransom Note
The ransom note created by Phenol ransomware is dropped as a file named Encrypt.html in affected directories:
You are encrypted!!!
Dear Sir/Madam,We are the PHENOL TeAm
1. All backup data and entire data are under our control.
2. Please contact us within 24 hours.
3. Please do not repair files or terminate related processes, otherwise it may become impossible to recover.
4. If cooperation goes well, we will not destroy, disclose or sell your data.
5. If you violate the above requirements, all data will be published on the Internet or provided to third party organizations and data recovery will not be provided.
Finally, please pay us a ransom of $5000 USDT within three days as requested
Email:Hulk67888@outlook.com
© 2025 Ransomware Co.
Best Practices to Protect Against Phenol Ransomware
- Always apply security patches to VPNs, firewalls, and endpoints.
- Enforce multi-factor authentication for all remote access.
- Maintain immutable and offline backups.
- Monitor outbound traffic for unauthorized exfiltration.
- Train employees on phishing awareness.
Conclusion: Restoring Operations After a Phenol Attack
Phenol ransomware poses severe risks due to its strong encryption and extortion tactics. While free decryption remains unlikely, professional solutions such as our Phenol Decryptor provide victims with a safer recovery path than paying ransoms. By combining proactive defense, immediate response, and expert recovery tools, organizations can mitigate damages and return to normal operations.
Frequently Asked Questions
Contact Us To Purchase The Phenol Decryptor Tool







One Comment