How to remove Prey (.prey35) ransomwar from Windows and servers?
Overview & Quick Facts
Prey is a MedusaLocker-family ransomware sample observed appending the extension .prey35 to encrypted files and dropping a desktop ransom note titled HOW_TO_RECOVER_DATA.html. The actors claim RSA + AES hybrid encryption and data exfiltration; they pressure victims with a 72-hour escalation window.
Related article: How to remove MedusaLocker (.stolen9 ransomware) from servers and NAS devices?
Immediate containment & evidence preservation (do these first)
- Disconnect affected systems from the network immediately to halt lateral spread.
- Preserve the ransom note, encrypted files and any logs or memory dumps—do not modify them.
- Do not reboot or format systems; avoid running unaudited third-party “fixes.”
- If possible, perform a non-destructive forensic image of affected disks for analysis.
Also read: How to Decrypt .bce0yUQslW.jj3 Files Encrypted by Proton / Shinra Ransomware?
Free and low-cost recovery options
Backup restore: The safest recovery path is restoring from verified, offline or immutable backups. Validate integrity (checksums/mount tests) before restoring to avoid reintroducing encrypted data.
VM snapshots: If pre-attack hypervisor snapshots exist (and were not reached by the attacker), rolling back can restore operations quickly. Confirm snapshot integrity and isolate them before use.
Known public decryptors & research tools: For some legacy MedusaLocker/related variants, community decryptors may exist. These tools are variant-specific and often do not apply to modern strains. Running an incorrect decryptor can corrupt files—test first on non-critical samples.
GPU-based research tools: Academic or open-source brute-force utilities (when applicable) have helped only where cryptographic seeds were weak or partially exposed. Such tools require significant GPU resources and are specialized (Linux/CUDA environments). They are rare solutions and are not guaranteed.
Paid & professional recovery routes
Paying the ransom (not recommended): Payment may yield a decryption utility but carries legal, ethical, and practical risks. Attackers may withhold keys or supply incomplete tools. Payment also funds criminal activity.
Third-party negotiators and incident responders: Experienced negotiators handle TOR communication and may secure test decryptions before payment. Professional responders combine containment, forensics, negotiation, and (if necessary) coordinated payment decisions. Fees and success rates vary.
Our commercial Prey decryptor & recovery service:
We offer a paid recovery service that follows the template’s workflow adapted for Prey-like incidents:
- Hybrid cloud analysis + integrity ledger: Encrypted file samples are processed in a secure sandbox; a tamper-evident ledger (blockchain audit) logs operations and verifies integrity of recovered artifacts.
- Ransom note ID mapping: The service maps the Victim/Login ID from the ransom note to the specific encryption batch used by the attackers, enabling targeted key retrieval or matching.
- Universal decryptor option: For cases without a ransom note, an advanced (premium) module attempts to handle recent variants using proprietary research and matching heuristics.
- Secure execution & non-destructive testing: Read-only prechecks assess decryptability; test decryptions of non-critical files are performed before full operations.
- Requirements: encrypted samples, ransom note (if present), admin access to affected systems or provided forensic images, and an internet connection for cloud processing.
Step-by-Step Prey Recovery Guide with Prey Decryptor
- Assess the Infection
Identify file extensions: .prey35, and confirm presence of HOW_TO_RECOVER_DATA.html ransom note. - Secure the Environment
Disconnect infected systems from the network immediately to stop Prey from spreading or encrypting shared drives. - Engage Our Recovery Team
Submit sample encrypted files along with the ransom note for variant verification, and we will begin analysis and share a detailed recovery timeline. - Run Our Decryptor
Launch the Prey Decryptor as an administrator for best performance. An internet connection is required since the tool connects to our secure recovery servers. - Enter Your Victim ID:
Find the Victim ID in HOW_TO_RECOVER_DATA.html and input it into the decryptor for accurate key mapping. - Start the Decryptor:
Begin the decryption process and allow the tool to safely restore your files to their original state.
Also read: How to Remove TENGU (.tengu) Ransomware and Recover Data?
How Prey behaves on an infected host?
Prey encrypts user files in place, renames them with the .prey35 suffix, replaces desktop wallpaper with its own message, and leaves a ransom note offering limited test decryptions. The actors warn against third-party tools and threaten data leaks if paid demands are not met.
Common initial infection paths
Prey spreads via social engineering and common malware distribution vectors: malicious email attachments (macro-enabled documents), bundled executables from untrusted sources (cracks, torrents), trojan loaders/backdoors, malicious web downloads and malvertising. Some strains also leverage removable drives and network shares for propagation.
Indicators of Compromise (IOCs)
Key artifacts to search for:
- File extension: .prey35
- Ransom note filename: HOW_TO_RECOVER_DATA.html
- Contact emails used by attackers: recovery2@salamati.vip, recovery2@amniyat.xyz
- Example detection labels: Avast — Win64:MalwareX-gen [Ransom]; ESET — Variant Of Win64/Filecoder.MedusaLocker.A; Microsoft — Ransom:Win64/MedusaLocker.MZT!MTB.
- Typical symptom: inability to open files that previously worked; ransom message on desktop.
Tactics, Techniques & Procedures (TTPs)
Prey follows the classic ransomware kill-chain:
- Initial compromise: phishing and trojans (user-triggered macros or malicious EXEs).
- Privilege escalation & persistence: attempts to gain admin privileges to access broader file systems.
- Lateral movement: targeting network shares and mapped drives to maximize impact.
- Data exfiltration: attacker claims to have copied sensitive files prior to encryption.
- Encryption & denial: hybrid RSA/AES encryption to lock files and destroy recovery options (e.g., shadow copy deletion is commonly observed in similar families).
Tools and auxiliary components observed
While Prey itself performs encryption, operators commonly deploy auxiliary tools and loaders:
- Loaders/backdoors: trojanized executables and remote access tools to install the ransomware.
- Credential stealers: utilities to harvest credentials for lateral movement.
- File transfer utilities: RClone, WinSCP, or similar tools are often used for exfiltration (noted practice in related incidents).
- Common AV detection names are useful for hunting on endpoints and AV telemetry.
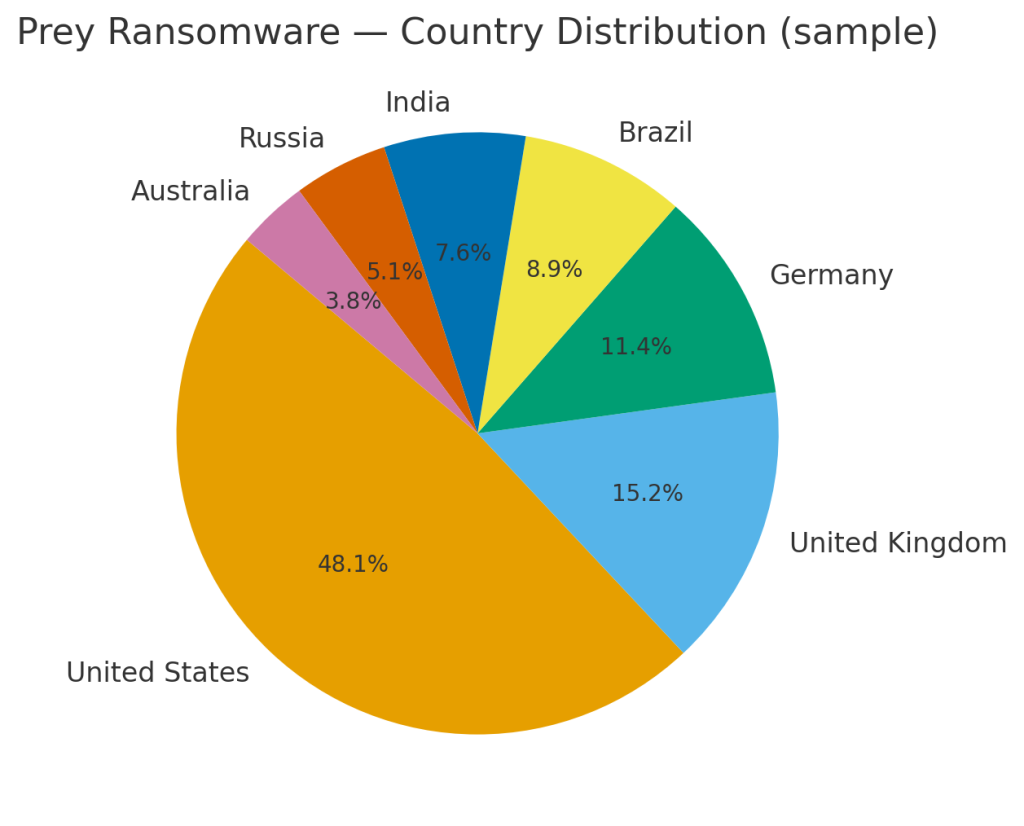
Victim profile
A. Country distribution
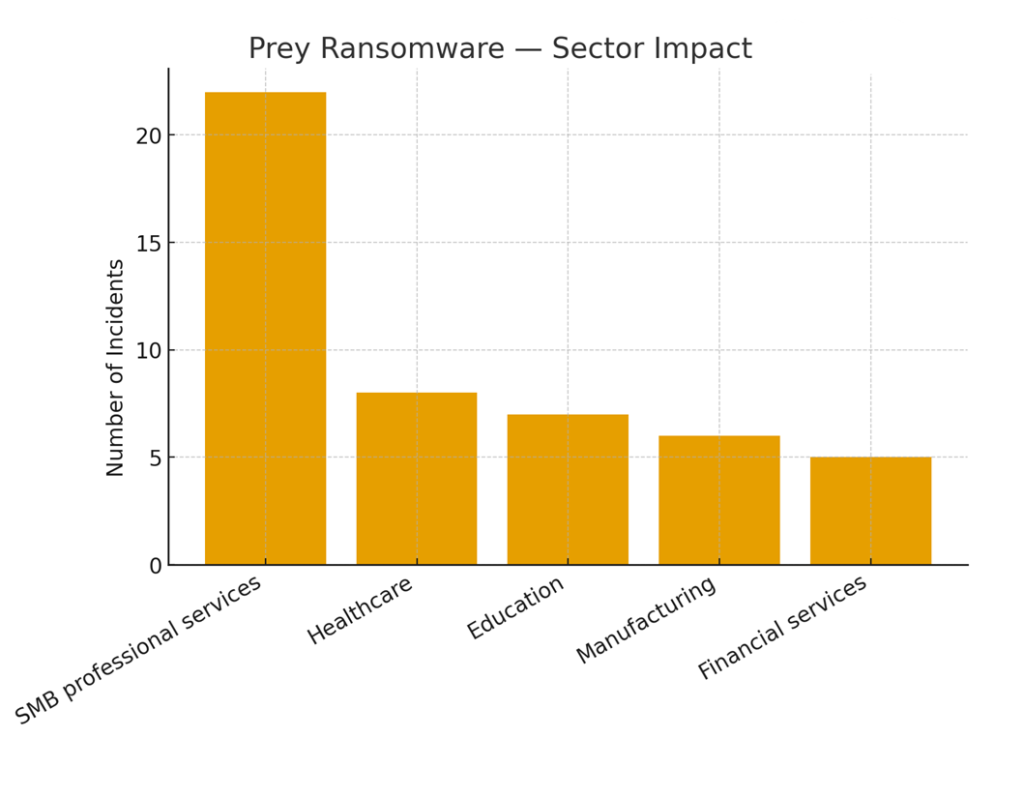
B. Example organizations / sectors impacted
C. Timeline
Removing Prey from infected systems
Use reputable antivirus/EDR to remove active ransomware components. Removal stops further encryption but does not restore already encrypted files. Preserve forensic images before cleanup. After removal, patch and reimage impacted hosts as required.
Hardening & prevention recommendations
Maintain multiple offline/immutable backups, enforce multi-factor authentication on remote access, apply critical patches promptly (especially VPN/firewall appliances), restrict use of unverified drivers, segment networks to limit lateral movement, and employ continuous monitoring or an MDR service.
Ransom note breakdown (what attackers claim)
The ransom note asserts a company network compromise, hybrid RSA+AES encryption of files, and stolen data held on a private server. It pressures victims with a 72-hour ransom increase and offers up to three free test decryptions for non-critical files.
YOUR COMPANY NETWORK HAS BEEN PENETRATED
Your files are safe! Only modified.(RSA+AES)
ANY ATTEMPT TO RESTORE YOUR FILES WITH THIRD-PARTY SOFTWARE WILL PERMANENTLY CORRUPT IT. DO NOT MODIFY ENCRYPTED FILES. DO NOT RENAME ENCRYPTED FILES.
No software available on internet can help you. We are the only ones able to solve your problem. We gathered highly confidential/personal data. These data are currently stored on a private server. This server will be immediately destroyed after your payment. If you decide to not pay, we will release your data to public or re-seller. So you can expect your data to be publicly available in the near future.. We only seek money and our goal is not to damage your reputation or prevent your business from running. You will can send us 2-3 non-important files and we will decrypt it for free to prove we are able to give your files back.
Contact us for price and get decryption software.
email:
recovery2@salamati.vip
recovery2@amniyat.xyz* To contact us, create a new free email account on the site: protonmail.com
IF YOU DON’T CONTACT US WITHIN 72 HOURS, PRICE WILL BE HIGHER.
Detection and hunting guidance
Hunt for sudden mass file renames ending in .prey35, new instances of HOW_TO_RECOVER_DATA.html, and outbound traffic to suspicious domains or email addresses listed in the note. Review endpoint process creation logs for suspicious loaders and scanning behavior on internal shares.
Conclusion & recommended next steps
Prey ransomware(.prey35) is a serious MedusaLocker-style threat that demands immediate containment, careful evidence preservation and a disciplined recovery plan. Begin with isolation and forensic preservation, then assess recovery options: verified backups first, professional analysis second, and consider paid recovery services only after weighing risks.
Frequently Asked Questions
Contact Us To Purchase The Prey Decryptor Tool