How to Decrypt .enc / .iv / .salt Ransomware and Recover Encrypted Files?
Professional Recovery Tool for .enc Ransomware
Our experts have engineered a decryptor specifically designed for ransomware that uses .enc, .iv, and .salt file extensions. This malware targets Windows, Linux, and virtualized environments such as VMware ESXi. Our decryptor is built for speed, security, and precision, ensuring maximum data restoration without corrupting files.
Related article: How to Unlock .Encrypt3 Files and Decrypt Mimic/Pay2Key Ransomware?
How Our Recovery Process Operates?
The decryption process combines artificial intelligence and blockchain validation to process encrypted data inside a secure environment. The blockchain ledger verifies integrity throughout the recovery. Each ransom note contains a login identifier, which our tool uses to align with the encryption keys applied during the attack. In cases where the ransom note is missing, we also offer an advanced decryption tool capable of handling the latest variants of this ransomware. Before recovery begins, the decryptor scans files in a read-only mode to ensure no additional damage occurs.
Also read: How to Decrypt Bruk Ransomware (.bruk) and Recover Encrypted Files?
Minimum Requirements for Using the Decryptor
To initiate recovery, victims must provide a copy of the ransom note titled Instruction-For Decrypt-READ-ME.txt, access to a few encrypted files, and administrative rights on the affected system. An internet connection is also necessary for secure processing and verification.
Immediate Steps After Detection
The first action is to disconnect the infected systems from the network to prevent the malware from spreading further. Victims must keep encrypted files intact and preserve ransom notes, logs, and network traffic dumps. Shutting down the compromised system without rebooting is recommended, as restarting may trigger additional encryption routines. Finally, it is crucial to contact a ransomware recovery expert rather than attempting random tools from unreliable forums, which can lead to permanent data loss.
Recovery Options and Decryption Methods
Free Solutions
Community Decryptors for Legacy Strains
Some cybersecurity researchers have developed tools for earlier versions of ransomware that use .enc extensions. These rely on weak cryptographic implementations discovered in older samples. Unfortunately, newer versions that also generate .iv and .salt files have corrected these flaws, leaving these free tools ineffective.
Restoring from Backup
Organizations that maintain secure offline or offsite backups have the cleanest recovery route. However, these backups must be validated carefully to ensure they were not tampered with during the attack. Immutable storage and snapshot technology provide the strongest resilience.
Virtual Machine Rollbacks
If virtual environments maintain pre-infection snapshots, infected machines can be rolled back quickly. These snapshots should be validated to confirm that the attackers did not delete or corrupt them.
Paid Solutions
Paying the Attackers
When a ransom is paid, victims typically receive a decryptor tied to their unique ID from the ransom note. This method is risky, as there is no guarantee that the criminals will deliver a functional tool. Even when provided, some attacker tools contain backdoors or result in incomplete decryption.
Third-Party Negotiation
Professional negotiators sometimes assist in ransom communications. Their experience helps validate attacker claims and can occasionally reduce ransom amounts. However, this process can be costly and time-consuming.
Our Specialized Decryptor
We provide a professionally engineered decryptor that leverages reverse-engineered flaws and secure cloud infrastructure. Encrypted files are processed in a sandbox, ensuring safety and accuracy. Audit logs are returned with each recovery session. Unlike attacker-provided tools, our decryptor avoids fraud and guarantees integrity.
Step-by-Step Guide to File Recovery
First, confirm the ransomware by checking file extensions such as .enc, .iv, or .salt, along with the ransom note. Next, isolate the environment and disable all active encryption scripts. After securing the system, submit a sample set of encrypted files and the ransom note to our recovery team for evaluation. Our experts will then provide a recovery roadmap. Once confirmed, our decryptor is launched with administrative privileges. Victim IDs are entered to align decryption keys, and the recovery process begins, restoring files to their original state.
Also read: How to Remove LockSprut Ransomware and Restore (.rupy3xz1) Encrypted Files?
Online and Offline Recovery Options
Offline recovery is suitable for air-gapped networks or sensitive infrastructures, where external transfers can be used for decryption. Online recovery provides faster turnaround by connecting securely to our servers with encrypted channels. Both methods are supported by our decryptor.
Technical Overview of the Ransomware
This ransomware family is known for combining multiple cryptographic elements during encryption. Files are renamed with .enc, while initialization vectors are stored in separate .iv files and salts in .salt files. This layered method complicates brute-force recovery. The ransom note Instruction-For Decrypt-READ-ME.txt guides victims to contact attackers through TOR-based communication channels.
In-Depth Attack Techniques and Tools Used
Attackers behind this ransomware exploit unpatched vulnerabilities, brute-force weak remote access points, and use phishing emails to gain entry. Common vulnerabilities in VPN appliances and RDP exposures are frequently exploited. Once inside, attackers rely on a range of tools to strengthen their foothold and maximize damage.
Mimikatz is used to extract plaintext passwords, hashes, and Kerberos tickets directly from system memory, enabling lateral movement and privilege escalation.
LaZagne serves as a lightweight alternative to harvest stored credentials from browsers, email clients, and system applications, giving attackers additional login access.
SoftPerfect Network Scanner is deployed to enumerate live hosts, open ports, and shared resources, providing attackers with a map of the internal infrastructure.
Advanced IP Scanner is similarly used to quickly identify accessible machines and administrative shares across the compromised network.
RClone facilitates stealthy data exfiltration by synchronizing stolen files with cloud storage providers, bypassing traditional detection mechanisms.
Mega.nz is another favored exfiltration service, offering encrypted cloud hosting that makes outbound traffic appear benign to security tools.
Ngrok enables attackers to create secure tunnels for remote access, disguising their command-and-control communication as normal encrypted traffic.
AnyDesk is leveraged for persistent remote desktop access, often installed as a legitimate tool to blend in with normal IT activity.
AdFind is used to query Active Directory for user accounts, group memberships, and system information, helping attackers escalate domain-wide privileges.
PCHunter64 provides low-level system inspection and manipulation, allowing attackers to terminate processes, disable protections, and tamper with system internals.
Zemana is misused in Bring-Your-Own-Vulnerable-Driver (BYOVD) attacks, where its kernel-level access is exploited to disable security controls and slip past defenses.
PowerTool acts as a rootkit utility, enabling attackers to manipulate hidden processes and drivers while staying invisible to endpoint monitoring systems.
Together, these tools form a complete offensive toolkit that covers credential theft, reconnaissance, persistence, exfiltration, and evasion, making the ransomware campaign highly disruptive and difficult to contain.
Encryption and Extortion Tactics
The ransomware uses a hybrid encryption scheme that pairs ChaCha20 or AES for file encryption with RSA for securing keys. This ensures that without the private keys, decryption is practically impossible. Shadow copies and local backups are deleted to cripple recovery attempts. Attackers then employ double extortion by threatening to leak stolen corporate data if the ransom is not paid.
Indicators of Compromise (IOCs)
Victims often find .enc, .iv, and .salt files across their systems. Suspicious outbound connections to services such as Ngrok, AnyDesk, or Mega.nz may appear. The ransom note is always named Instruction-For Decrypt-READ-ME.txt. Executables often run from temporary directories and leave behind process manipulation artifacts.
Defensive Measures and Best Practices
Securing VPN access with multi-factor authentication, patching vulnerable software, and segmenting networks significantly reduces attack surface. Disabling unnecessary remote access services and monitoring for anomalous traffic also improves resilience. Kernel-level protections can help defend against the use of malicious drivers. Continuous monitoring and threat detection provide the most reliable long-term defense.
Victimology and Impact Assessment
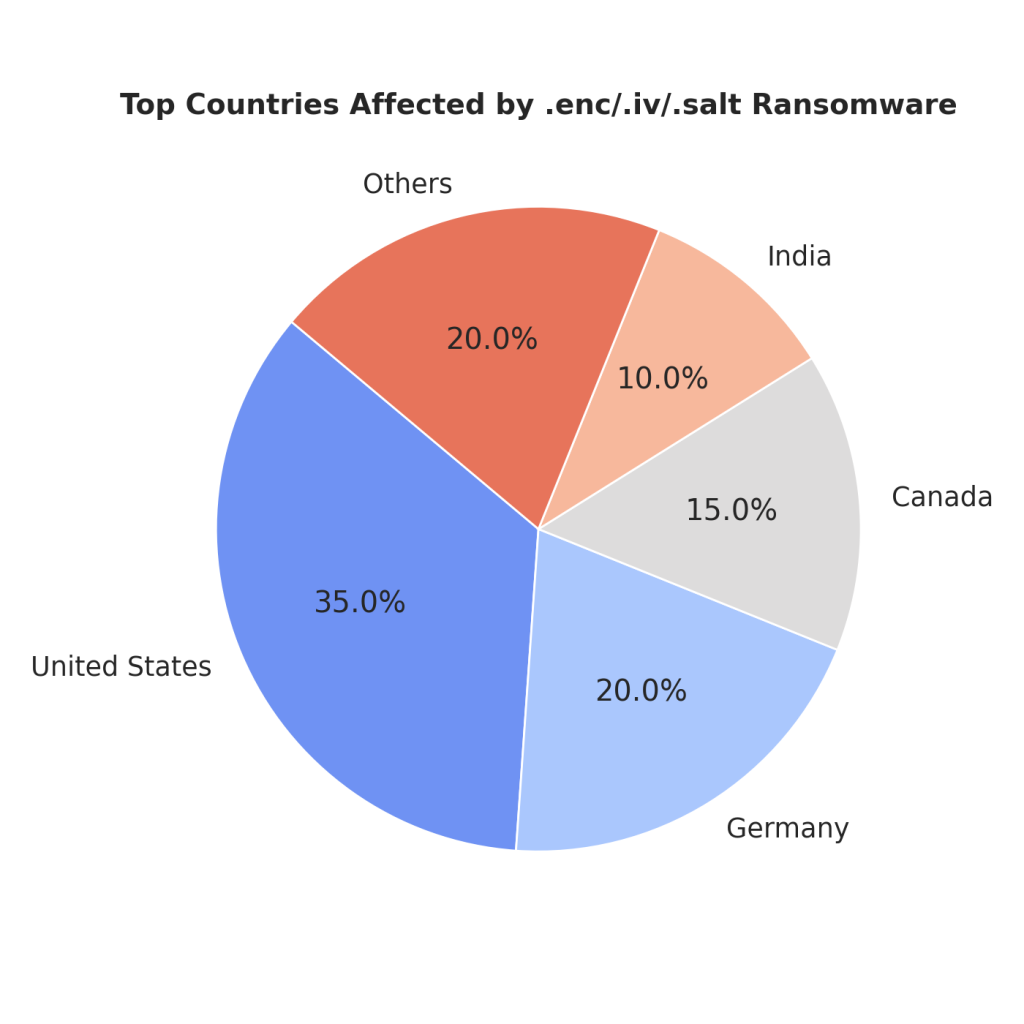
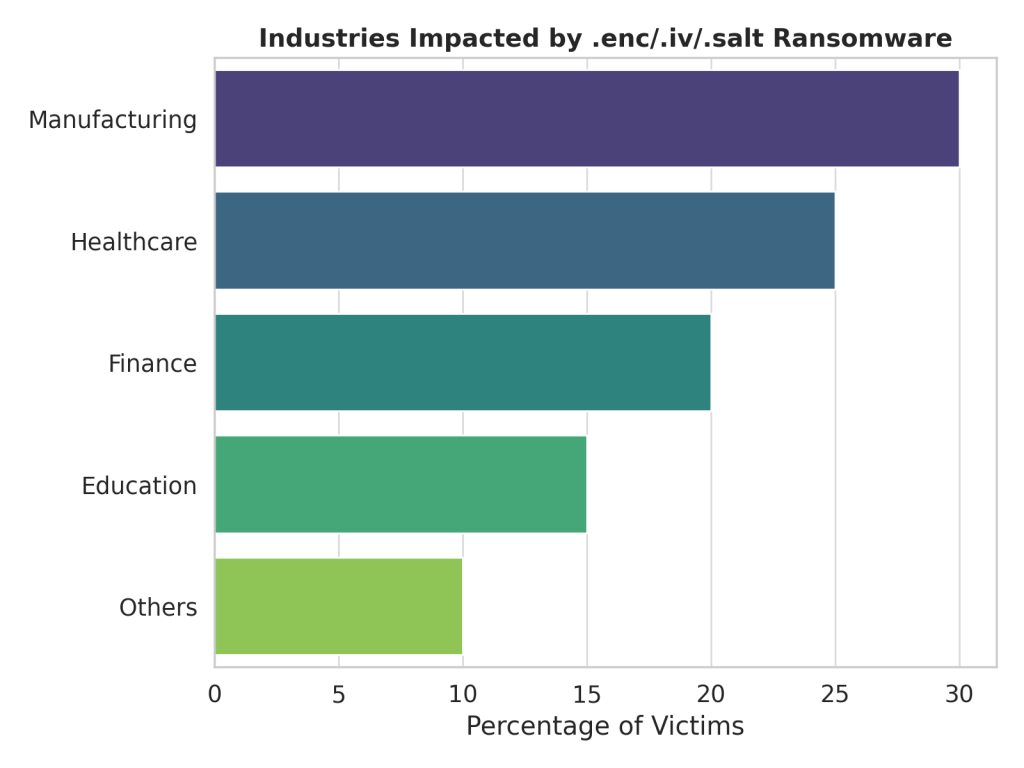
This ransomware has primarily targeted enterprises in manufacturing, healthcare, finance, and education sectors. It has also been active against government organizations. Countries with high infection rates include the United States, Germany, Canada, and India.
- Top Countries Impacted:
- Industries Affected:
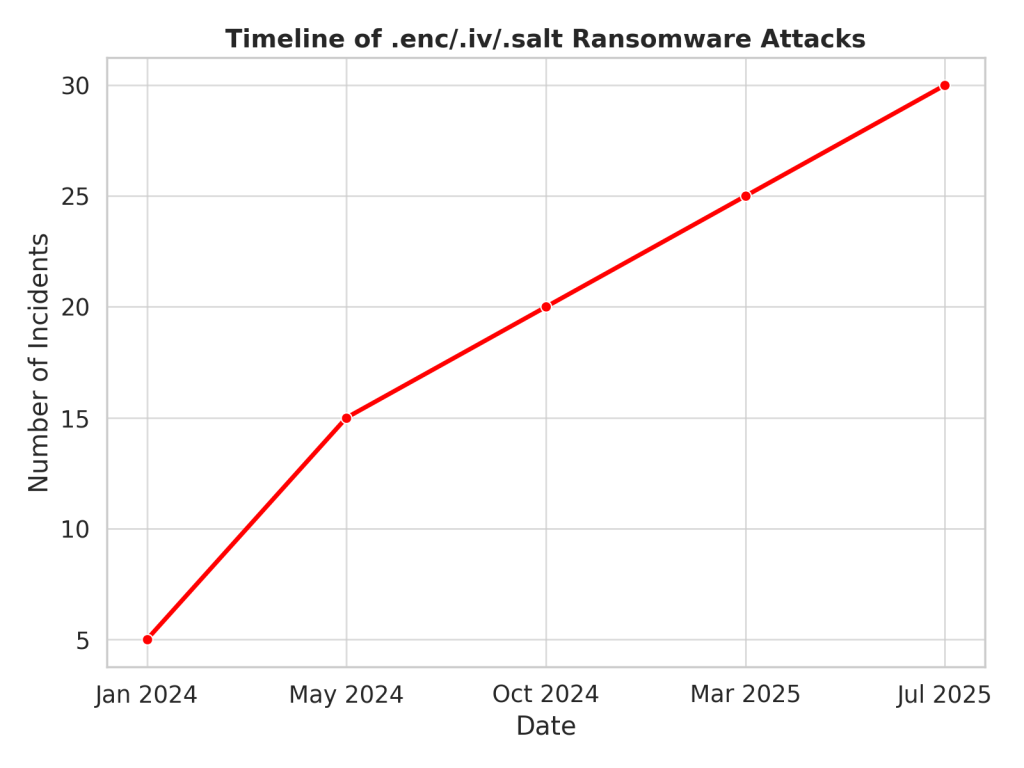
- Timeline of Attacks:
Anatomy of the Ransom Note
The ransom note typically informs victims that backups have been deleted and sensitive data exfiltrated. Attackers stress that paying the ransom saves time and money, while failing to cooperate results in stolen data being leaked on underground forums. Victims are directed to TOR portals where a unique login code is used to initiate negotiation.
Excerpt from the ransom note:
– Your data has been stolen and encrypted
– Your data will be published online if you do not pay the ransom.
>>>> What guarantees that we will not scam you?
We are not driven by political motives; we only want your money.
If you pay, we will give you the decryption tools and erase your data.
Life is too short to worry. Don’t stress, money is just paper.
If we don’t provide you with the decryption tools or fail to delete your data after payment, no one will pay us in the future.
Our reputation is crucial to us. We attack companies worldwide and no one has been dissatisfied after paying.
You need to contact us and decrypt one file for free using your personal HWID
Download and install the qTOX from https://qtox.github.io/en.html
Write to us in the chat and wait for a response. We will always reply.
Sometimes, there might be a delay because we attack many companies.
Tox ID : 3683A5F20609D00437ADEF76C55167C40C30B2BBF106D1F38103EA7DCF5FE87F568EEDC0565C
Your personal HWID: “xkjRCaFeLEhiBc2p1WGbEd9MjjW3t1AZmt3Lnv5zPLk6V7dcwW”
>>>>How to Pay Us?
To pay us in Bitcoin (BTC), follow these steps:
– Obtain Bitcoin: You need to acquire Bitcoin. You can buy Bitcoin from an exchange playform like Coinbase, Binance, or Kraken.
Create an account, verify your identity, and follow the instructions to purchase Bitcoin.
– Install a Bitcoin Wallet: If you don’t already have a Bitcoin wallet, you’ll need to install one.
Some popular options include Electrum, Mycelium, or the mobile app for Coinbase. Follow the instructions to set up your wallet.
– Send Bitcoin to Us: Once you have Bitcoin in your wallet, you need to the required amount to our Bitcoin address.
Open your wallet, select the “Send,” and enter our Bitcoin address, which you will receive through our TOR chat or secure communication channels.
Make sure to double-check the address before sending.
– Confirm Payment: After you’ve send the Bitcoin, notify us through the TOR chat with the transaction ID.
We will verify the payment and provide you with the decryption tools and confirm the deletion of your data.
Remember, time is of the essence. Delays in payment could result in permanent data loss or additional attacks.
>>>>Warning! Do not DELETE or MODIFY any files, it could cause recovery issues!
>>>>Warning! If you do not pay the ransom, we will repeatedly attack your company!
Additional Insights on Evolution
Researchers believe this ransomware is an evolution of earlier strains that used simpler AES encryption and lacked .iv and .salt metadata files. The newer versions show advanced cryptographic handling and improved persistence, suggesting that the developers are professionalized groups rather than amateurs.
Conclusion
The .enc, .iv, and .salt ransomware presents a severe risk to organizations worldwide. While it employs advanced encryption and extortion techniques, recovery is possible with expert assistance. Victims should avoid panic, secure their systems, and pursue legitimate decryption solutions. Our decryptor has already restored critical systems for several organizations, providing a safer alternative to paying criminals.
Frequently Asked Questions
Contact Us To Purchase The .enc Decryptor Tool







2 Comments