How to Decrypt .obscura Extension Files Infected by Obscura Ransomware?
Our Obscura Decryptor: Rapid Recovery, Expert-Engineered
Our cybersecurity research team reverse-engineered the Obscura ransomware family — a newly emerging strain that uses modern XChaCha20 encryption with Curve25519 key exchange — and built a decryptor tailored for enterprise recovery. Designed for Windows, Linux, and VMware ESXi environments, our decryptor focuses on reliability, speed, and precision to help organizations restore critical systems without ransom payments.
Related article: How to Decrypt .enc / .iv / .salt Ransomware and Recover Encrypted Files?
How It Works?
- AI + Blockchain Analysis: Your encrypted files are securely uploaded to our isolated recovery environment. Blockchain-based validation ensures recovered data maintains integrity.
- Login ID-Based Mapping: Each ransom note (README_Obscura.txt) contains unique victim identifiers. Our tool matches these IDs to the corresponding encryption batch for targeted decryption.
- Universal Key Mode (Optional): If the ransom note is missing, our premium decryptor leverages algorithmic flaws and forensic pattern matching to attempt universal recovery.
- Secure Execution: Files are scanned in read-only mode before decryption begins, reducing the risk of corruption.
Also read: How to Decrypt H2OWATER Team Ransomware and Recover Encrypted Files?
Requirements
To use our Obscura decryptor, you’ll need:
- A copy of the ransom note (README_Obscura.txt)
- Access to encrypted files (with .obscura extension or containing OBSCURA! footer)
- Stable internet connection for cloud-based processing
- Local or domain administrator privileges
Immediate Steps to Take After Obscura Ransomware Attack
Disconnect Immediately
Isolate infected machines from the network to stop NETLOGON replication and scheduled task propagation. Obscura abuses C:\WINDOWS\sysvol\sysvol\[domain].local\scripts\ to spread across domain controllers.
Preserve Everything
Do not delete ransom notes or encrypted files. Keep forensic artifacts like event logs, scheduled task details, and file hashes (c00a2d757349bfff4d7e0665446101d2ab46a1734308cb3704f93d20dc7aac23) for analysis.
Immediately Shut Down Compromised Systems
Do not reboot infected systems — Obscura may attempt shadow copy deletions (vssadmin delete shadows /all /quiet) or restart encryption scripts.
Contact a Ransomware Recovery Expert
Avoid random “free decryptors” from shady forums. Work with trusted ransomware experts who have analyzed Obscura’s unique encryption markers and infection tactics.
How to Decrypt Obscura Ransomware and Recover Your Data?
Obscura is one of the most aggressive new ransomware families of 2025. It uses strong modern cryptography and advanced persistence mechanisms (NETLOGON, scheduled tasks, RDP enablement). If your systems are locked, our Obscura Decryptor provides the safest route to recovery — engineered specifically for this strain.
Obscura Decryption and Recovery Options
1. Free Methods
Backup Restore
- How It Works: Offline or air-gapped backups remain the most reliable recovery path. If Obscura failed to encrypt or delete backup storage, you can restore clean images.
- Integrity Verification: Validate snapshots before restoring — Obscura is known to terminate backup services like Veeam, Acronis, Datto, and SQLSERVERAGENT.
- Immutable Storage Advantage: WORM/cloud retention backups are far less vulnerable to Obscura’s destructive attempts.
VM Snapshots
- Rollback from Pre-Infection: VMware ESXi and Proxmox snapshots can rapidly roll back systems.
- Isolation Required: Confirm snapshot integrity; Obscura operators may have accessed vCenter or deleted snapshot logs.
- Retention Settings Matter: Hourly/daily snapshots provide far stronger resilience.
2. Paid Methods
Paying the Ransom
- Victim ID Validation: Each ransom note ties a victim ID to an encryption key stored on the attacker’s TOR server.
- Risks: No guarantee the attackers will deliver a working decryptor. Tools may corrupt files or carry backdoors.
- Legal Issues: Paying may breach compliance laws (HIPAA, GDPR) and fund cybercrime.
Third-Party Negotiators
- Intermediary Bargaining: Some firms negotiate with attackers to reduce ransom demands.
- Ransom Validation: Negotiators often request “test decryptions” to confirm legitimacy.
- High Costs: Services may charge retainers or percentages of ransom amounts.
Our Specialized Obscura Ransomware Decryptor
After extensive research into Obscura’s cryptography and system behavior, our team developed a proprietary Obscura decryptor.
How It Works?
- Reverse-Engineered Utility: Built from cryptographic flaws in Obscura’s XChaCha20 implementation.
- Cloud-Based Decryption: Files processed in isolated recovery nodes, integrity verified with blockchain.
- Fraud Risk Mitigation: We provide references, case studies, and do not require upfront payment until feasibility is confirmed.
Step-by-Step Obscura Recovery Guide with Obscura Decryptor
- Assess the Infection
- Look for ransom note README_Obscura.txt.
- Confirm file footers containing OBSCURA!.
- Look for ransom note README_Obscura.txt.
- Secure the Environment
- Disconnect infected systems.
- Disable suspicious scheduled tasks (SystemUpdate, iJHcEkAG).
- Disconnect infected systems.
- Engage Our Recovery Team
- Submit ransom note + encrypted samples for analysis.
- Submit ransom note + encrypted samples for analysis.
- Run Our Decryptor
- Launch with admin privileges.
- Enter victim ID (from ransom note).
- Start decryption and monitor recovery logs.
- Launch with admin privileges.
Also read: How to Unlock .EXTEN Files and Decrypt EXTEN Ransomware?
Offline vs Online Decryption Methods
- Offline: Best for air-gapped or classified environments. Files decrypted via external drive transfer.
- Online: Faster, includes live support and real-time verification.
Our decryptor supports both options.
What is Obscura Ransomware?
Obscura is a new ransomware variant first detected in August 2025. It rapidly gained notoriety after targeting healthcare, manufacturing, utilities, and real estate sectors worldwide.
How Obscura Works: Inside Look
- Initial Access: Likely via compromised accounts, RDP enablement, or lateral movement.
- Propagation: Abuse of NETLOGON SYSVOL replication to distribute payloads across domain controllers.
- Privilege Escalation: Binary checks for Administrator rights before running.
- Defense Evasion: Kills >120 processes (AV/EDR, SQL, Veeam, Splunk, Crowdstrike Falcon).
- Impact: Encrypts files with XChaCha20, appends OBSCURA! footer, deletes shadow copies, and leaves ransom notes.
Known Obscura Indicators of Compromise (IOCs)
- SHA256 (Ransomware Executable):
c00a2d757349bfff4d7e0665446101d2ab46a1734308cb3704f93d20dc7aac23 - Ransom Note: README_Obscura.txt
- Leak Site Onion:
obscurad3aphckihv7wptdxvdnl5emma6t3vikcf3c5oiiqndq6y6xad.onion - Suspicious Paths:
C:\WINDOWS\sysvol\sysvol\[domain].local\scripts\ - Scheduled Tasks:
SystemUpdate, iJHcEkAG
Mitigations and Best Practices
- Restrict NETLOGON writes to admins only.
- Monitor scheduled tasks for suspicious names.
- Alert on vssadmin commands deleting shadow copies.
- Patch and harden systems; enforce MFA for RDP.
- Implement continuous monitoring via SOC/MDR services.
Statistics and Facts So Far Regarding Obscura Ransomware
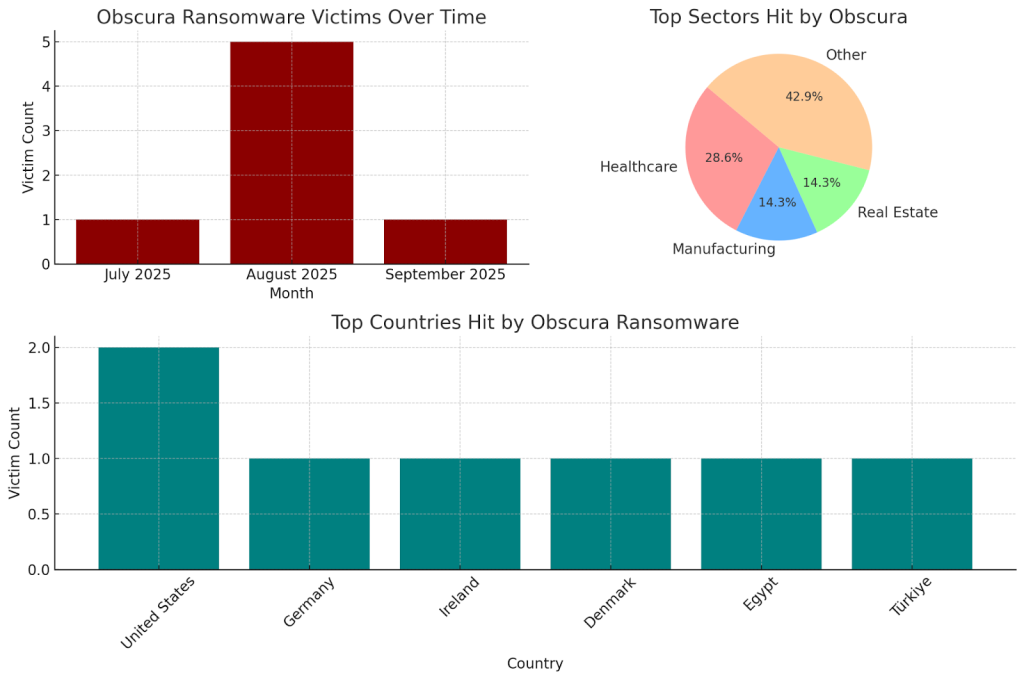
- First Discovered Victim: July 2025
- Publicly Listed Victims: 7 (as of Sept 5, 2025)
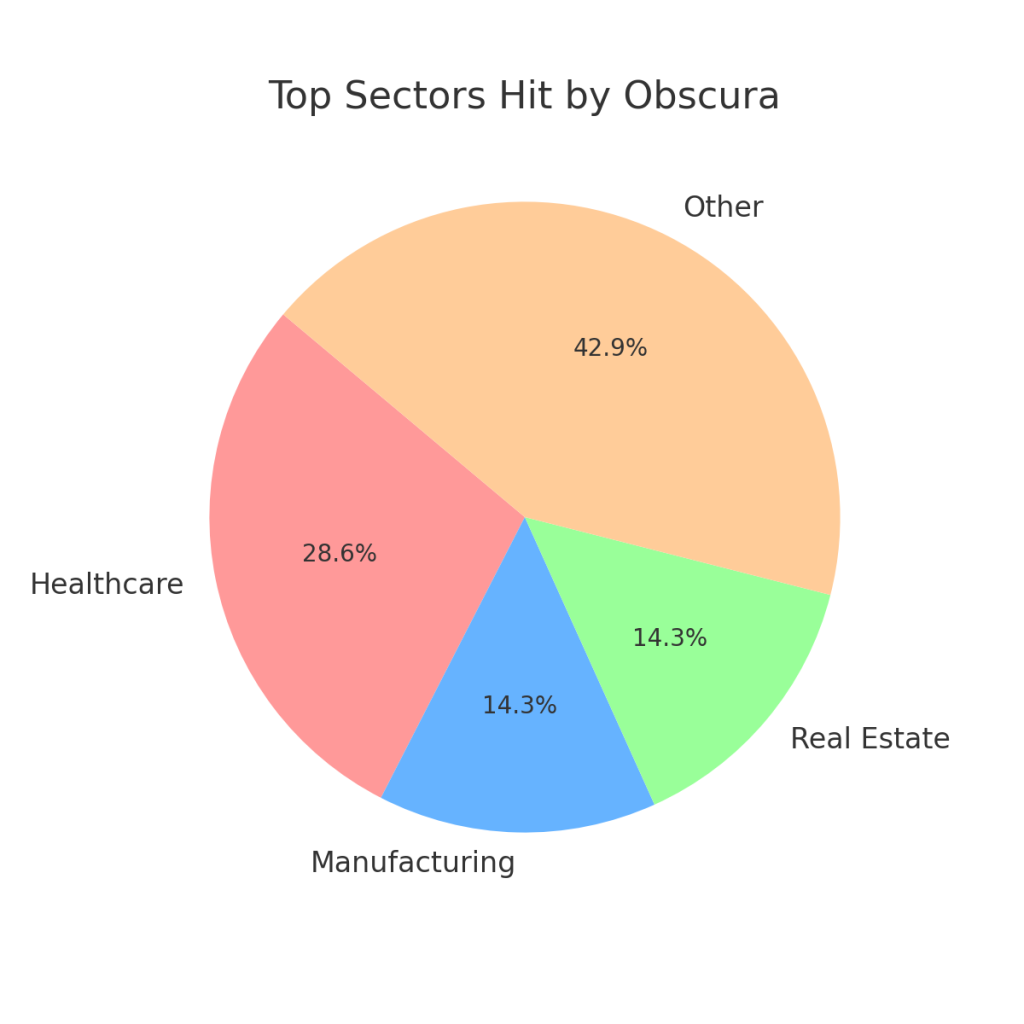
- Top Sectors Hit: Healthcare, Manufacturing, Real Estate
- Top Countries: US, Germany, Ireland, Denmark, Egypt, Türkiye
Obscura Ransomware Victims Over Time
Top Sectors Hit by Obscura
Top Countries Hit by Obscura Ransomware
Ransom Note Dissected: What They Say and Why
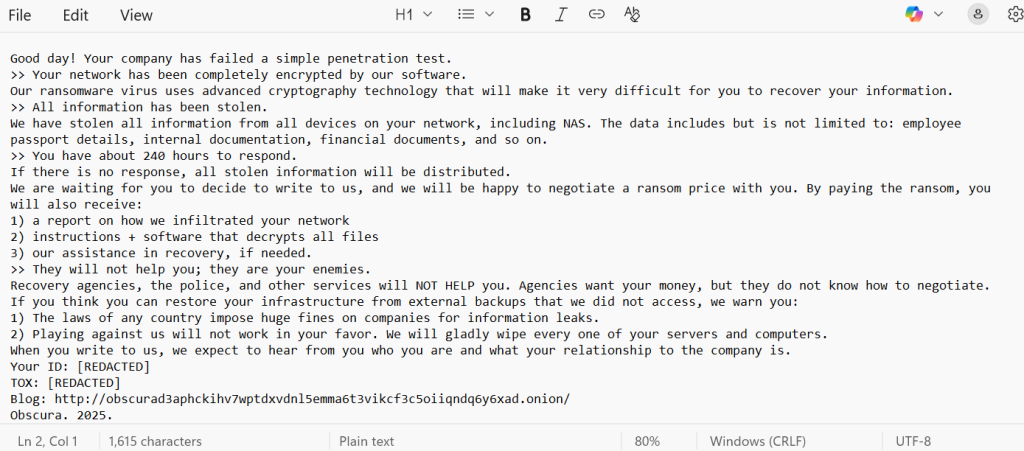
The ransom note README_Obscura.txt typically states:
Good day! Your company has failed a simple penetration test. >> Your network has been completely encrypted by our software. Our ransomware virus uses advanced cryptography technology that will make it very difficult for you to recover your information. >> All information has been stolen. We have stolen all information from all devices on your network, including NAS. The data includes but is not limited to: employee passport details, internal documentation, financial documents, and so on. >> You have about 240 hours to respond. If there is no response, all stolen information will be distributed. We are waiting for you to decide to write to us, and we will be happy to negotiate a ransom price with you. By paying the ransom, you will also receive: 1) a report on how we infiltrated your network 2) instructions + software that decrypts all files 3) our assistance in recovery, if needed. >> They will not help you; they are your enemies. Recovery agencies, the police, and other services will NOT HELP you. Agencies want your money, but they do not know how to negotiate. If you think you can restore your infrastructure from external backups that we did not access, we warn you: 1) The laws of any country impose huge fines on companies for information leaks. 2) Playing against us will not work in your favor. We will gladly wipe every one of your servers and computers. When you write to us, we expect to hear from you who you are and what your relationship to the company is. Your ID: [REDACTED] TOX: [REDACTED] Blog: http://obscurad3aphckihv7wptdxvdnl5emma6t3vikcf3c5oiiqndq6y6xad.onion/ Obscura. 2025.
Conclusion: Restore Your Data, Reclaim Your Network
Obscura ransomware may look like an unstoppable new player, but with the right tools and response strategy, recovery is possible. Avoid fake decryptors and panic-driven ransom payments. Trust verified methods and expert support.
Our Obscura Decryptor has already been validated against real-world samples. Whether you’re facing enterprise-wide downtime or localized disruption, our recovery specialists are ready.
Frequently Asked Questions
Contact Us To Purchase The Obscura Decryptor Tool







2 Comments