Lockis Ransomware (.lokis) GlobeImposter Recovery and Decryption Guide 2025
A new and insidious ransomware variant, identified as Lockis, has been discovered by security researchers analyzing samples on VirusTotal. This malware is a member of the notorious GlobeImposter family, known for its strong encryption and double extortion tactics. Lockis encrypts files and appends the .lockis extension, leaving behind an HTML ransom note titled how_to_back_files.html. The attackers threaten to leak stolen data if the ransom is not paid, creating immense pressure on victims.
This guide provides a comprehensive, step-by-step playbook for understanding the Lockis threat, containing the infection, and exploring every viable pathway to recover your data and protect your organization’s reputation without paying the ransom.
Related article: How to Recover Data from Ripper (.ripper12, .ripper20, .ripper32, MedusaLocker Ransomware?
Threat Summary Table
| Attribute | Detail |
|---|---|
| Threat Name | Lockis Ransomware |
| Threat Type | Ransomware, Crypto Virus, Files Locker |
| Family | GlobeImposter |
| Encrypted Files Extension | .lockis |
| Ransom Demanding Message | how_to_back_files.html |
| Free Decryptor Available? | No (As of this writing) |
| Ransom Amount | Varies, increases after 72 hours. |
| Cyber Criminal Contact | karloskolorado@tutanota.com, bugervongir@outlook.com, Tor Chat |
| Detection Names | Avast (Win32:dUmPeX [Susp]), ESET-NOD32 (Win32/Filecoder.FV Trojan), Kaspersky (Trojan-Ransom.Win32.Purgen.ard), Microsoft (Ransom:Win32/Filecoder.DLK!MTB) |
Decoding the Threat: The Lockis Ransom Note
The Lockis attackers use an HTML ransom note to deliver their demands, which adds a layer of perceived professionalism. The note is direct, issuing clear warnings and instructions to maximize the psychological impact on the victim.
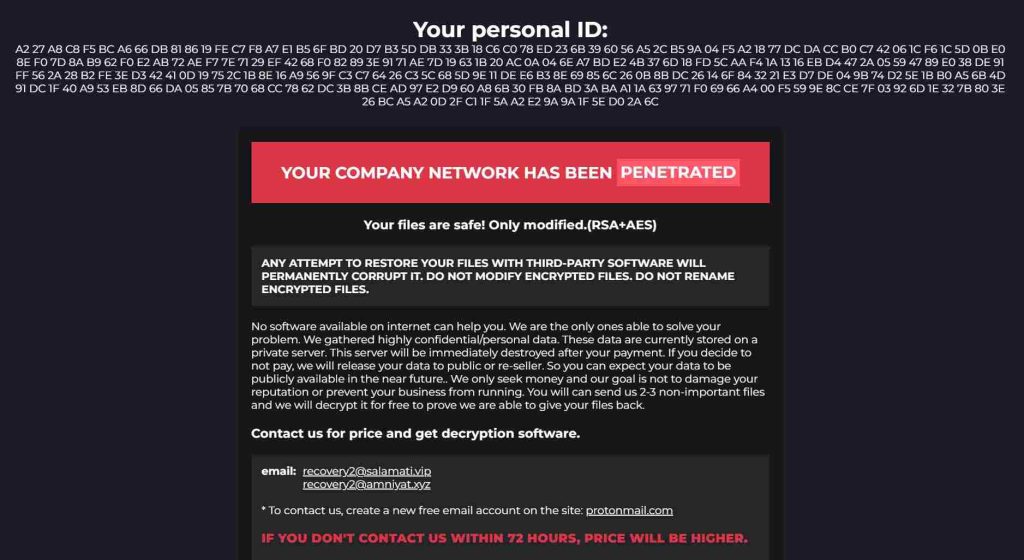
The text presented in the ransom note reads as follows:
YOUR PERSONAL ID: - /!\ YOUR COMPANY NETWORK HAS BEEN PENETRATED /!\ All your important files have been encrypted! Your files are safe! Only modified. (RSA+AES) ANY ATTEMPT TO RESTORE YOUR FILES WITH THIRD-PARTY SOFTWARE WILL PERMANENTLY CORRUPT IT. DO NOT MODIFY ENCRYPTED FILES. DO NOT RENAME ENCRYPTED FILES. No software available on internet can help you. We are the only ones able to solve your problem. We gathered highly confidential/personal data. These data are currently stored on a private server. This server will be immediately destroyed after your payment. If you decide to not pay, we will release your data to public or re-seller. So you can expect your data to be publicly available in the near future.. We only seek money and our goal is not to damage your reputation or prevent your business from running. You will can send us 2-3 non-important files and we will decrypt it for free to prove we are able to give your files back. Contact us for price and get decryption software. .onion * Note that this server is available via Tor browser only Follow the instructions to open the link: 1. Type the addres "https://www.torproject.org" in your Internet browser. It opens the Tor site. 2. Press "Download Tor", then press "Download Tor Browser Bundle", install and run it. 3. Now you have Tor browser. In the Tor Browser open .onion 4. Start a chat and follow the further instructions. If you can not use the above link, use the email: karloskolorado@tutanota.com bugervongir@outlook.com * To contact us, create a new free email account on the site: protonmail.com IF YOU DON'T CONTACT US WITHIN 72 HOURS, PRICE WILL BE HIGHER.
Also read: eCh0raix Ransomware Recovery Guide: Decrypt Your Synology NAS Files Without Paying
Indicators of Compromise (IOCs) and Attack Behavior
Recognizing the signs of a Lockis infection is the first critical step. The malware’s distinct file extension, its connection to the GlobeImposter family, and its double extortion tactic are its most obvious fingerprints.
Indicators of Compromise (IOCs):
- File Extension: The most obvious indicator is the appended
.lockisextension to all encrypted files (e.g.,document.pdfbecomesdocument.pdf.lockis). - Ransom Note File: The presence of an HTML file named
how_to_back_files.htmlon the desktop and in encrypted folders. - Contact Information: The note provides specific email addresses (
karloskolorado@tutanota.com,bugervongir@outlook.com) and instructions to use a Tor-based chat site. - Double Extortion Tactic: The explicit claim of data exfiltration and the threat to publish or sell it is a key behavioral indicator.
Tactics, Techniques, and Procedures (TTPs) with MITRE ATT&CK Framework:
- Initial Access (TA0001): Lockis, like other ransomware, gains entry through common vectors. These include phishing emails with malicious attachments, exploiting outdated software vulnerabilities, pirated programs, key generators, and malicious ads.
- Execution (TA0002): Once the user executes the malicious file, the ransomware payload is activated, beginning its encryption routine across the system’s drives.
- Impact (TA0040): The primary impact is data encryption using a strong RSA+AES hybrid. The secondary, and often more damaging, impact is data exfiltration for double extortion, threatening to publish sensitive data if the ransom is not paid.
The Recovery Playbook: A Multi-Path Approach to Data Restoration
This core section outlines the primary methods for recovering your encrypted data.
Path 1: The Direct Decryption Solution
The most direct path to recovery is using a tool specifically designed to reverse the encryption.
Our Specialized Lockis Decryptor
Our team has developed a specialized decryptor to counter the Lockis threat. By leveraging advanced cryptographic analysis and pattern recognition, our tool can often reconstruct the decryption keys without needing to interact with the attackers.
Step-by-Step Guide:
- Step 1: Assess the Infection: Confirm that files have the
.lockisextension and verify the presence of thehow_to_back_files.htmlfile. - Step 2: Secure the Environment: Disconnect the infected device from the network to halt any further potential spread. It is critical to remove the malware from your system first.
- Step 3: Submit Files for Analysis: Send a few encrypted samples (under 5MB) and the ransom note file to our team. This allows us to confirm the Lockis variant and build an accurate recovery timeline.
- Step 4: Run the Lockis Decryptor: Launch the tool with administrative privileges. The decryptor connects securely to our servers to analyze encryption markers and file headers.
- Step 5: Enter the Victim ID: While the note shows a blank ID, our tool may generate a unique profile based on the file structures to begin the decryption process.
- Step 6: Automated File Restoration: Once initiated, the decryptor verifies file integrity and restores data automatically.
Also read: DataKill Ransomware Decryption: Forensic Recovery Guide
Public Decryption Tools and Repositories
If our tool is not applicable, several public initiatives are invaluable. Always identify the ransomware strain before using any tool, as running the wrong decryptor can cause permanent damage.
- ID Ransomware Service: Use the free ID Ransomware service to upload the ransom note and a sample encrypted file. The service will identify the strain and tell you if a known decryptor exists. Find it at ID Ransomware.
- The No More Ransom Project: This is the most important resource, providing a centralized repository of free decryption tools. Visit their Decryption Tools page and search for “Lockis” or “GlobeImposter”.
- Major Security Vendor Decryptors:
- Emsisoft: Renowned for its ransomware expertise, Emsisoft offers a variety of decryptors. Check their website for available tools at Emsisoft Decryptors.
- Kaspersky: Through its No Ransom portal, Kaspersky provides the latest decryptors and removal tools. Visit Kaspersky No Ransom.
- Avast: Provides numerous free ransomware decryption tools. Find them on the Avast Ransomware Decryption Tools page.
- Trend Micro: Offers a Ransomware File Decryptor for numerous known ransomware families. You can download it from the Trend Micro website.
Path 2: The Gold Standard – Backup Restoration
If a decryptor is unavailable, restoring from a backup is the most reliable method.
Enterprise-Grade Backups: Veeam
For businesses, Veeam is a market leader in backup and recovery solutions, offering robust protection against ransomware. Veeam can create immutable backups that cannot be altered by the ransomware and offers specialized recovery processes like Cleanroom Recovery to prevent reinfection. Learn more at the official Veeam website.
Cloud and Native Backups
- Microsoft OneDrive: If you use OneDrive, you may be able to restore your files using its Version History feature.
- Windows File Versions (Shadow Copies): Lockis likely attempts to delete these, but sometimes remnants remain. To check, right-click on an encrypted file, select
Properties, and go to thePrevious Versionstab.
Path 3: Last Resort – Data Recovery Software
This method has a low probability of success with modern ransomware like Lockis but can be a lifeline if no backups exist.
- EaseUS Data Recovery Wizard: A user-friendly tool that can recover lost, deleted, or formatted data. You can download it from the EaseUS website.
- Stellar Data Recovery: A powerful recovery application known for its scanning capabilities. Find it at the Stellar Data Recovery official site.
- Recuva: A free and effective tool for recovering deleted files. Download it from CCleaner’s official site.
Important Procedure: Install the data recovery software on a separate, clean computer. Then, connect the infected hard drive to it as an external drive.
Path 4: System Repair and Diagnostics
These tools can help you get your system running so you can perform other recovery steps.
Hiren’s BootCD PE
This is a bootable Windows PE that contains a suite of useful tools for system recovery and repair. You can download it from the official Hiren’s BootCD website.
Comprehensive Alternatives to Hiren’s BootCD PE
- MediCat USB: A highly-regarded and extremely comprehensive bootable toolkit.
- Sergei Strelec’s WinPE: A popular and powerful alternative based on a Windows PE environment.
- SystemRescue: A Linux-based rescue system designed for repairing unbootable computers and recovering data. Find it at the SystemRescue website.
- Ultimate Boot CD (UBCD): A veteran, free bootable recovery disk that consolidates numerous diagnostic and repair tools.
Path 5: Specialized Virtualization Recovery (If Applicable)
If your virtual machines were hosted on an ESXi or Hyper-V server and were targeted, the recovery process is more complex.
- Specialized Software Tools: Tools like DiskInternals VMFS Recovery™ are designed to recover VMDK images. You can find them at the DiskInternals website.
- Forensic Data Extraction: Tools like DMDE (DM Disk Editor) can sometimes reconstruct files from partially encrypted disks. Find it at the DMDE website.
- Hypervisor-Specific Tools: For specific strains that target ESXi, tools like CISA’s ESXiArgs-Recover Script can be used.
Path 6: Network Storage Recovery (If Applicable)
If the ransomware encrypted files on a NAS or DAS device, the recovery options differ from a standard Windows PC.
- Public Decryption Tools: Reiterate the importance of using the No More Ransom Project and vendor tools.
- Leveraging Built-in Features: The most effective method for NAS devices is Snapshots. Brands like Synology and QNAP have a snapshot feature that can revert shared folders to a state just minutes before the attack.
- Cloud Sync Versioning: If your NAS was configured to sync files to a cloud service, you may be able to use the version history features of those services to restore your files.
Essential Incident Response and Prevention
A full response includes containment, eradication, and future prevention.
Containment and Eradication
- Isolate the Infected System: Immediately disconnect the machine from the network to prevent the ransomware from spreading.
- Remove the Malware: Use a reputable antivirus or anti-malware program to scan for and remove the ransomware executable.
- Change All Passwords: Assume that credentials have been compromised and change passwords for all user accounts, especially administrators, and for any network services or cloud accounts.
Hardening Your Defenses with Modern Protection
- Endpoint Protection Platforms (EPP/EDR): Solutions like SentinelOne Singularity™ Endpoint and CrowdStrike Falcon focus on preventing ransomware by identifying and neutralizing threats using behavioral AI.
- Integrated Cyber Protection: Tools like Acronis Cyber Protect combine a traditional antivirus with integrated backup and recovery.
- The 3-2-1 Backup Rule: Maintain at least three copies of your data, on two different types of media, with one copy stored off-site or in the cloud.
- Employee Training: Conduct regular security awareness training to teach staff how to spot phishing emails and malicious links.
- Patch Management: Regularly patch all systems and software to close vulnerabilities that ransomware can exploit.
Post-Recovery: Securing Your Environment and Ensuring Resilience
This critical phase begins after your files have been restored.
- Step 1: Verify Data Integrity and Completeness: Check restored files for corruption and completeness by opening a sample from different directories and file types.
- Step 2: Conduct a Full, Deep System Scan: Run a full, deep scan of your entire system using a reputable antivirus or anti-malware solution.
- Step 3: Fortify All Credentials: Change all user, admin, service, and cloud passwords. Enforce the use of strong, unique passwords for every account.
- Step 4: Patch and Update Everything: Update the OS and all third-party applications to close security holes that the attackers may have exploited.
- Step 5: Reconnect to the Network Cautiously: Monitor for unusual activity upon reconnection.
- Step 6: Implement or Strengthen a 3-2-1 Backup Strategy: Create or improve a robust backup system and test it regularly.
- Step 7: Perform a Post-Incident Analysis: Review how the attack happened. Use this knowledge to improve user training and security policies.
Reporting Obligations
Report the incident to help combat cybercrime and fulfill potential legal obligations.
- Report to Law Enforcement: In the US, file a complaint with the FBI’s IC3. In the UK, report to Action Fraud.
- Report to CISA: The U.S. Cybersecurity & Infrastructure Security Agency (CISA) urges reporting via its portal.
Conclusion
The Lockis ransomware represents a significant threat due to its strong encryption, its connection to the established GlobeImposter family, and its aggressive double extortion tactics. However, like all ransomware, it can be defeated with a calm, methodical, and prepared response. The path to resilience begins long before an attack occurs. Investing in a multi-layered security posture that combines advanced endpoint protection, robust network security, and a disciplined 3-2-1 backup strategy is the most effective defense. Paying the ransom only fuels the criminal ecosystem and offers no guarantee of a positive outcome.
By understanding the tactics of threats like Lockis and preparing accordingly, you can transform a potential catastrophe into a manageable incident, ensuring that your data—and your peace of mind—remain secure.
Frequently Asked Questions (FAQ)
Contact Us To Purchase The Lockis Decryptor Tool






2 Comments