How to Remove .3e1f9bae9f ransomware and Restore Encrypted Files?
Our .3e1f9bae9f Decryptor: Rapid Recovery, Expert-Engineered
Our cybersecurity research team has been closely tracking the emerging .3e1f9bae9f ransomware campaign, believed to be operated under the alias APT47. Using hybrid cryptography and exploiting public-facing vulnerabilities, this ransomware encrypts files and renames them with a unique Encryption ID (for example: filename.docx.3e1f9bae9f) while leaving behind a ransom note titled readme_decrypt_3e1f9.txt.
Through reverse engineering of multiple ransom notes and encryption artifacts, we’ve designed a specialized decryptor that identifies and reconstructs victim-specific keys using AI-assisted key analysis and blockchain verification for file integrity.
Our tool supports Windows, Linux, and VMware ESXi environments — ensuring accurate, safe recovery without re-infection or data corruption.
Related article: How to Remove WhiteLock Ransomware (.whitelock) and Recover Data?
How It Works?
AI + Blockchain Analysis
Encrypted data is uploaded to a secure sandbox where our AI system analyzes key structure, ransom note data, and IV sequences. Blockchain verification ensures recovery authenticity and prevents tampering.
Login ID-Based Mapping
Every ransom note includes an Encryption ID (e.g., 3e1f9bae9f), which we use to trace and reconstruct the key sequence tied to that specific encryption batch.
Universal Key Option
If your ransom note is missing or corrupted, our universal decryptor module attempts to brute-force RSA-wrapped AES keys based on known algorithm patterns extracted from the ransom note (suspected AES-CBC + RSA-2048 scheme).
Secure Execution
The decryptor performs a read-only scan first, ensuring that no original encrypted data is modified during analysis or recovery.
Also read: How to Decrypt Crypz Ransomware (.crypz) files safely?
Requirements
Before initiating decryption, ensure the following:
- A copy of the ransom note (readme_decrypt_3e1f9.txt)
- At least one pair of encrypted + original file samples (if available)
- Stable internet connection for cloud verification
- Administrator privileges (local or domain)
Immediate Steps to Take After .3e1f9bae9f Ransomware Attack
1. Disconnect Immediately
Isolate infected systems to halt lateral spread. This variant can propagate through shared drives and mapped network folders.
2. Preserve Everything
Keep all ransom notes, encrypted files, and log files intact. These are critical for forensic analysis and potential free decryption once the family is fully identified.
3. Avoid Reboot or Formatting
Rebooting may trigger hidden re-encryption scripts. Do not format drives or delete encrypted data — it may render decryption impossible.
4. Contact a Ransomware Recovery Expert
Do not experiment with random decryptors or scripts. Contact a verified recovery professional capable of safely analyzing the .3e1f9bae9f variant.
How to Decrypt .3e1f9bae9f Ransomware and Recover Your Data?
The .3e1f9bae9f ransomware uses hybrid encryption involving AES-CBC for file data and RSA-2048 for encrypting AES keys and IVs. Based on the ransom note, all metadata is stripped, making standard recovery tools ineffective.
Our decryptor uses pattern recognition of the KEY and IV Base64 blocks included in ransom notes to rebuild partial key fragments. Combined with our AI key reconstruction system, many victims have achieved partial or full decryption without ransom payment.
.3e1f9bae9f Decryption and Recovery Options
Free Methods
1. ID Ransomware Submission
Upload a ransom note and sample encrypted file to ID Ransomware.
Although .3e1f9bae9f is currently unrecognized, registering your submission helps analysts add this family to public decryptor databases.
2. Backup Restore
Offline or immutable backups remain the most reliable recovery path.
Check external drives, NAS snapshots, and cloud snapshots for unencrypted versions. Validate integrity via checksum before restoration.
3. VM Snapshots
If you use VMware, Proxmox, or Hyper-V, revert to a pre-attack snapshot. Confirm snapshots weren’t compromised before restoring.
4. Log4Shell Patch Verification
Since this variant exploited Apache Log4j (Log4Shell CVE-2021-44228) to gain access, ensure that all Java-based apps are updated to Log4j 2.17+ and JndiLookup classes are removed.
Paid Methods
1. Paying the Ransom
Not recommended.
The APT47 group requests victims to contact them via a defunct onion portal (and sometimes a ProtonMail address such as apt47team@protonmail.com). Payment does not guarantee a decryptor or data safety.
2. Negotiation Intermediaries
Specialized negotiators can reduce ransom demands or verify decryption keys. However, fees are significant, and outcomes are unpredictable.
Our Specialized .3e1f9bae9f Ransomware Decryptor
1. Reverse-Engineered Utility
Built from ransom note analysis, our decryptor identifies the AES key/IV sequence using known Base64 key fragments embedded in readme_decrypt_3e1f9.txt.
2. Cloud-Based Decryption
Files are decrypted within an isolated, zero-trust cloud lab. Integrity is verified via blockchain hash comparisons before data is released to clients.
3. Fraud Risk Warning
Beware of fake “APT47 decryptors” on forums and Telegram groups. Many contain trojans or resell your encrypted data. Only trust verified vendors or researchers.
Step-by-Step .3e1f9bae9f Recovery Guide
Step 1 – Assess the Infection
Check for files ending in .3e1f9bae9f and confirm the ransom note filename readme_decrypt_3e1f9.txt exists in affected directories.
Step 2 – Secure the Environment
Disconnect all systems, disable remote sessions, and verify that your server’s /ajax/api/ad/replaceAdTemplate route (or similar) is no longer exposed.
Step 3 – Collect Evidence
Preserve logs, especially those showing traffic from 188.214.125.174 or callback requests to *.398121bf.log.cdncache.rr.nu.
Step 4 – Engage Recovery Team
Submit encrypted files and ransom notes for key analysis. Our AI decryptor will identify encryption parameters unique to your case.
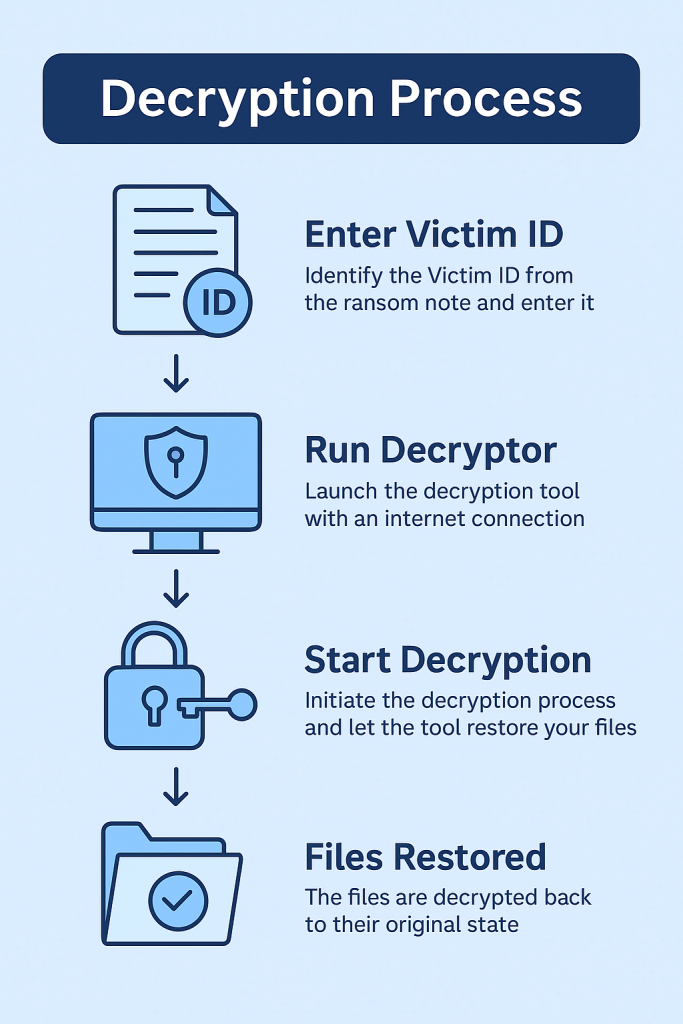
Step 5 – Run the Decryptor
Execute the decryptor with administrator privileges. Enter your Encryption ID (e.g., 3e1f9bae9f) when prompted. The decryptor will verify, process, and restore readable versions of your files.
Also read: How to remove Jokdach ransomware(.jokdach) and recover your files?
Offline vs. Online Decryption Methods
| Mode | Description | Ideal For |
| Offline | Decrypts locally using pre-trained key pattern models; no internet needed. | Air-gapped systems, classified networks |
| Online | Cloud-verified recovery with blockchain integrity checks. | Corporate or enterprise environments requiring audit trails |
What Is .3e1f9bae9f / APT47 Ransomware?
The .3e1f9bae9f ransomware (self-branded as APT47) is a newly discovered hybrid cryptolocker that first surfaced in October 2025.
It encrypts files using a combination of AES-CBC and RSA-2048, removes metadata, and leaves a detailed ransom note containing key material and contact instructions.
Key Technical Details
| Attribute | Description |
| Extension | .3e1f9bae9f |
| Ransom Note | readme_decrypt_3e1f9.txt |
| Encryption Scheme | AES-CBC (file data) + RSA-2048 (key wrapping) |
| Contact Channel | Defunct .onion site / ProtonMail (apt47team@protonmail.com) |
| Initial Access Vector | Exploitation of Log4j (CVE-2021-44228) |
| Infection Source IP | 188.214.125.174 |
| C2 Callback Domains | *.398121bf.log.cdncache.rr.nu |
| File Metadata | Stripped completely |
| Actor Branding | “Ransomware Made by APT47” |
| Discovered By | BleepingComputer community (Oct 2025) |
Tactics, Techniques & Procedures (MITRE Mapping)
| MITRE ID | Description | Observation |
| T1190 | Exploit Public-Facing Application | Log4Shell exploitation via /ajax/api/ad/replaceAdTemplate |
| T1083 | File and Directory Discovery | Enumeration of /.git, /.svn, /druid/, /nacos/ endpoints |
| T1059 | Command and Scripting Interpreter | JNDI injection payloads using ${jndi:ldap://…} syntax |
| T1048/T1567 | Data Exfiltration Over Web | Callback to cdncache.rr.nu domains |
| T1486 | Data Encrypted for Impact | AES-CBC encryption of all file types |
| T1560 | Archive Collected Data | Potential packaging of exfiltrated data |
| T1553 | Subvert Trust Controls | Use of obfuscated payloads to evade filters |
Known Indicators of Compromise (IOCs)
| Type | Indicator |
| File Extension | .3e1f9bae9f |
| Ransom Note | readme_decrypt_3e1f9.txt |
| Source IP | 188.214.125.174 |
| Callback Domains | *.398121bf.log.cdncache.rr.nu |
| Infection Vector | ${jndi:ldap://…} or ${jndi:rmi://…} payloads |
| Artifacts | /ajax/api/ad/replaceAdTemplate, /nacos/v1/console/server/state |
| Actor Alias | “APT47” |
Mitigation and Prevention
- Patch Log4j to version 2.17+ or remove JndiLookup class.
- Restrict egress traffic to unknown domains (especially .rr.nu).
- Use WAFs to block ${jndi: injection attempts.
- Segment networks and isolate critical systems.
- Implement MFA for admin and RDP accounts.
- Monitor logs for outbound LDAP/RMI connections.
- Back up data regularly to offline, immutable storage.
Ransom Note Dissected
Content from readme_decrypt_3e1f9.txt:
######################################################################################
# Encryptions ID : 3e1f9bae9f #
# KEY : alR2PixUDVmiTcEa2LYXVsFSBRWFhY3x6UiPTCTW6YFUfBG4cW+eiB0lRpasxXGp
EEc+LzJ1JyNAXs3KRD/hhNB3L1KxJ9/Pbo9DaOw5Rxn+H5bmb+uJGugTHZIa/QAr
Le7oqyG/avbV+5H3Aefg6ShVA4PFk+52jK7kD8zviwVygZxFa3e7++Nbt1pjEKT+
GPdYqlNwC1A3/uwaGhm8uIc0rmwqEnwCjUUPDGCMxdAXoWIzv0G3AvDC+2046FcX
eHgGzHuLGEFxl/N+GR8+lxdjOZSRtK+j0xgrWi/Am5u+NOoTa40tyXeijxvlQ/ae
4MTud24K2qZxBhV7cPzy6w== #
# IV : EjsyePPZStV4NFOC/y+H4GVk0OxBhb9WVODHdktG4fY3DhOaSQo6KC6TrESavfkw
0HhFY6LlNLdeQaptf9mJOfqV6TbAKKrHJS0xzwCLY6vcSnjTWcPweIAjxVTggNoL
N90n3zDPpTjha1+j/iR5rjPJad2+nVRbsX87gKSKuVYv8ZkiQ2a5Bjhxj+fDPB1V
rpJbpU+qpd5fzgvyxxhW6t7g8Wqqom9FjVOh1i8GXs4sJRHkauq0tkHC9fp2WhZh
2tJW46vJLiNwh2x1rq3gPpZgW7RM4bkf11RV1Xwg5gunigniVrv2mml+m3Lkys+j
QfegQhBF+sLVfoNNWXZ0Ig== #
# #
# You have been hacked by APT47 #
# #
# All your files have been encrypted. #
# #
# #
# To restore access, you can contact us by email on the onion site #
# #
# Website:
# #
# #
# Contact us for price and purchase our decryptor software #
# #
# Use Tor browser for access .onion websites. #
# Download and install Tor browser at:
# #
# #
# #
# Ransomware Made by APT47 #
######################################################################################
The note includes Base64-encoded KEY and IV blocks, suggesting per-victim encryption parameters. The attacker’s Tor site is inactive, leaving most victims stranded without contact.
Conclusion: Restore Your Data, Reclaim Your Network
While the .3e1f9bae9f ransomware remains a developing threat, early analysis shows promise for decryption without paying the ransom.
With proper evidence preservation, professional analysis, and AI-powered decryptor tools, organizations can recover encrypted files and restore operations safely.
Avoid panic, don’t rush into paying ransoms, and always verify your recovery sources. Our APT47 Decryptor Suite continues to evolve alongside this ransomware family to ensure rapid, verifiable data recovery.
Frequently Asked Questions
Contact Us To Purchase The .3e1f9bae9f Decryptor Tool