How to Decrypt .bSobOtA1D / .babyk Ransomware and Recover Files?
Our cybersecurity team has analyzed ransomware incidents involving .bSobOtA1D and .babyk extensions — linked to LockBit 3.0 Black and Babuk Locker families. Through extensive reverse-engineering of LockBit and Babuk encryption routines, we’ve built a specialized decryptor platform capable of safely identifying and restoring encrypted data across Windows, Linux, and VMware ESXi systems.
Our goal is fast, secure, and verifiable data recovery — minimizing downtime and data loss for victims affected by these high-impact ransomware strains.
Related article: How to Decrypt FIND Ransomware (.FIND) Files Safely?
How It Works?
1. Hybrid Signature Detection
The decryptor analyzes encrypted file headers, ransom note identifiers, and the unique 9-character extension (e.g., .bSobOtA1D) to determine if the infection stems from LockBit 3.0 or Babuk codebases. This is crucial since both may coexist, and double-encryption cases require precise order of decryption.
2. AI-Assisted Key Profiling
Our AI models compare encrypted samples against a vast ransomware encryption fingerprint database. Using entropy analysis and known cryptographic flaws from older LockBit and Babuk builds, the system attempts partial key reconstruction where feasible.
3. Cloud-Based Recovery Sandbox
Encrypted files are processed in isolated, read-only environments. Decryption attempts run through secure cloud nodes with real-time verification of file integrity and SHA256 hash consistency before any data is written back.
4. Dual-Path Algorithm
If a single variant (LockBit 3.0 Black) is detected, the decryptor applies AES/ChaCha20 + RSA key-pair reconstruction logic.
If dual infection (LockBit + Babuk) is confirmed, the decryptor initiates a two-stage recovery: outer decryption followed by Babuk-layer decryption.
Also read: How to Decrypt XxzeGRBSr (.XxzeGRBSr) Ransomware Files?
Requirements
Before starting the recovery process, ensure the following items are available:
- A copy of the ransom note (<random_ID>.README.txt, How_To_Restore_Your_Files.txt, or similar).
- Several encrypted files (preferably smaller than 1 MB).
- Administrative access on the infected system.
- Internet connectivity for optional cloud-based decryption checks.
- For forensic analysis, preserve logs and do not delete the encrypted files or ransom notes.
Immediate Steps to Take After .bSobOtA1D / .babyk Ransomware Attack
1. Disconnect Immediately
Physically isolate infected machines. LockBit 3.0 and Babuk both propagate through network shares, remote services, and domain controllers.
2. Preserve Everything
Do not rename or delete encrypted files or ransom notes. Preserve system logs, network captures, and malware binaries for analysis. These can help determine if files are doubly encrypted or corrupted.
3. Shut Down Compromised Systems Safely
Avoid rebooting or formatting. Many ransomware families re-encrypt or destroy data upon reboot. Capture volatile evidence first if possible.
4. Contact a Ransomware Recovery Expert
DIY attempts or shady decryptors can permanently corrupt files. Consult recognized cybersecurity recovery services to safely assess decryptability.
How to Decrypt .bSobOtA1D / .babyk Files and Recover Your Data?
The .bSobOtA1D and .babyk ransomware infections appear to be hybrid LockBit 3.0 Black and Babuk Locker operations. Both employ strong encryption — but some builds have exhibited flaws exploitable for partial recovery.
Decryption and Recovery Options
1. Free Methods
LockBit 3.0 Decryptor (When Available)
Earlier LockBit and Babuk decryptors released by law enforcement and vendors (like Avast or Kaspersky) can occasionally decrypt older or flawed variants. Always verify through NoMoreRansom.org before attempting decryption.
Babuk Legacy Decryptor
Some older Babuk samples from 2021–2022 used weak key derivation; the public Babuk decryptor may recover .babyk files if they belong to an older branch. However, modern Babuk 2.0 variants remain undecryptable without private keys.
2. Backup Restoration
If your backups are offline or immutable, restoring from them is the safest and fastest route. Verify integrity before restoration, as LockBit often attempts to encrypt or delete shadow copies and connected backups.
3. Virtual Machine Snapshots
VMware ESXi or Hyper-V snapshots created before infection can be reverted quickly to restore functionality. Ensure snapshots were not deleted or tampered with by the ransomware before rollback.
4. Third-Party Negotiators
If no decryption method exists, professional ransomware negotiators can mediate contact with attackers. They verify decryptor legitimacy through test file decryption before any payment. Negotiators also help navigate legal restrictions and insurance reporting obligations.
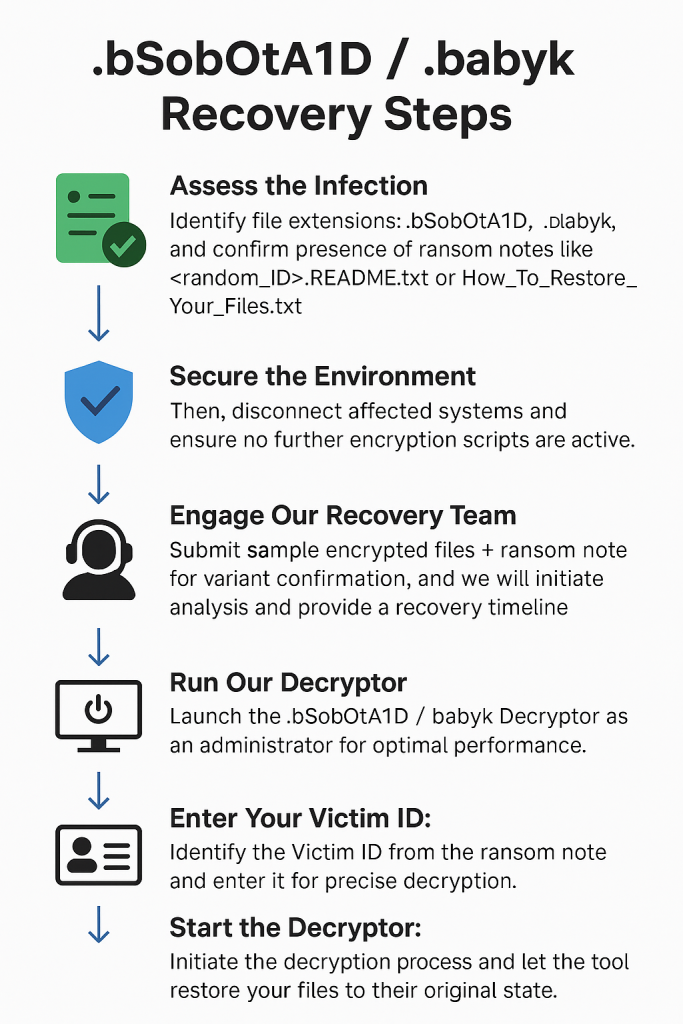
Step-by-Step .bSobOtA1D / .babyk Recovery Guide with Our Decryptor
Assess the Infection
Identify file extensions: .bSobOtA1D, .babyk, and confirm the presence of ransom notes like <random_ID>.README.txt or How_To_Restore_Your_Files.txt.
Secure the Environment
Then, disconnect affected systems and ensure no further encryption scripts are active.
Engage Our Recovery Team
Submit sample encrypted files + ransom note for variant confirmation, and we will initiate analysis and provide a recovery timeline.
Run Our Decryptor
Launch the .bSobOtA1D / .babyk Decryptor as an administrator for optimal performance.
An internet connection is required as the tool connects to our secure servers.
Enter Your Victim ID:
Identify the Victim ID from the ransom note and enter it for precise decryption.
Start the Decryptor:
Initiate the decryption process and let the tool restore your files to their original state.
Also read: How to Decrypt .ZuI7Kx3T3 Files Encrypted by LockBit 3.0 / Black ransomware?
Offline vs Online Decryption Methods
Offline Methods: These are ideal for air-gapped or sensitive environments. They only require external drive transfer and a secure boot system.
Online Methods: These provide faster recovery and live expert support, just like our .bSobOtA1D / .babyk Decryptor. These methods require an encrypted channel and a secure file upload.
Our decryptor supports both modes — offering flexibility for enterprise, government, and industrial infrastructure.
Technical Profile: .bSobOtA1D / .babyk Ransomware
1. Likely Families
- .bSobOtA1D → LockBit 3.0 Black (LockBit Black)
- .babyk → Babuk / Babuk-derived variant
2. Common Ransom Note Names
- LockBit: <random_ID>.README.txt
- Babuk: How To Restore Your Files.txt, RestoreFiles.txt, Help_Readme.txt, Recover_Your_Files.html
3. Typical Message Contents
- Unique victim ID.
- TOR address or .onion chat portal.
- Instructions for test decryption.
- Threats of data publication (“double extortion”).
4. Encryption Methods
- LockBit 3.0 uses hybrid ChaCha20 + RSA-2048 encryption.
- Babuk employs Elliptic Curve Diffie-Hellman (ECDH) and ChaCha8 for speed and strength.
- Double infections may result in nested encryption layers — requiring specialized sequence decryption.
Tools, TTPs & MITRE ATT&CK Mapping
| Tactic | Technique & Example Tools |
| Initial Access | Exploiting RDP/VPN (CVE-2023-4966 Citrix Bleed), phishing, drive-by downloads |
| Credential Access | Mimikatz, LaZagne, PowerShell secrets extraction |
| Execution | PowerShell, Cobalt Strike, custom loaders |
| Persistence | Task Scheduler entries, registry run keys |
| Lateral Movement | SMB propagation, PsExec, Group Policy deployments |
| Defense Evasion | Zemana driver exploit, BYOVD attacks, disabling AV |
| Exfiltration | RClone, WinSCP, Mega.nz, Ngrok |
| Impact | ChaCha20 + RSA file encryption, shadow copy deletion |
Known Indicators of Compromise (IOCs)
| Type | Example / Description |
| File Extensions | .bSobOtA1D, .babyk |
| Ransom Note Names | <random_ID>.README.txt, How_To_Restore_Your_Files.txt |
| Registry Keys Modified | HKCU\Software\LockBit\ or HKLM\Software\Babuk\ |
| Processes Killed | sqlservr.exe, vssvc.exe, msftesql.exe, backup.exe |
| Network Artifacts | TOR addresses, C2 endpoints on dark web |
| Encryption Signature | Randomized 9-char ID appended to files (LockBit pattern) |
Mitigation and Prevention
- Patch and Update all systems, especially VPNs, Citrix, and RDP endpoints.
- Use MFA for all administrative and remote accounts.
- Isolate critical backups in offline or immutable storage.
- Monitor for unusual outbound traffic to TOR relays or Mega.nz.
- Implement EDR/XDR solutions capable of detecting ransomware behavior in real time.
- Conduct regular incident response drills to reduce downtime.
Ransom Note Dissected: What They Say and Why
Victims typically find ransom notes such as:
“All your files have been encrypted with a unique key.
To restore them, visit our portal on TOR: [random onion address].
Test decryption available for 1–2 files.
Do not modify or rename encrypted data, or you risk permanent loss.”
This language mirrors LockBit’s structured negotiation model and Babuk’s recovery instructions — both referencing TOR portals and private keys stored remotely.
Statistics and Activity Overview
- LockBit 3.0 remains the most active RaaS worldwide through 2025.
- Babuk derivatives resurfaced on ESXi and Linux systems throughout 2024–2025.
- Hybrid cases (like .bSobOtA1D + .babyk) may result from multi-stage infections or affiliate overlaps within the ransomware ecosystem.
Conclusion: Restore Your Data, Reclaim Your Network
The .bSobOtA1D / .babyk ransomware attack represents a complex threat combining the speed of LockBit 3.0 Black with the persistence of Babuk Locker.
While full decryption is rarely possible without the attackers’ keys, forensic preservation, controlled recovery, and expert decryptor evaluation can often restore critical data and prevent further loss.
Frequently Asked Questions
Contact Us To Purchase The babyk Decryptor Tool