How to Decrypt BB Ransomware (.BB) and Recover Locked Data?
Overview
BB is a crypto-ransomware strain in the MedusaLocker family that encrypts user data and appends the extension .BB to every affected file (for example photo.jpg → photo.jpg.BB). Victims find a ransom note file named Recovery_Instructions.html in every folder where files were encrypted.
The ransom note lists Tor links and two contact emails (dec_helper@excic.com and dec_helper@dremno.com) and demands payment in Bitcoin (example demand: 0.3 BTC). The attackers claim files were encrypted with RSA + AES and threaten to increase the price after 72 hours.
Related article: How to remove 0xxx Ransomware (.0xxx) and restore your data?
Practical first actions after you discover BB encryption
- Disconnect the infected machines: from the network immediately (pull network cables or disable NICs).
- Preserve evidence: do not delete the ransom note or modify encrypted files; collect logs, network captures, and system hashes.
- Power state: avoid rebooting critical machines unless instructed by incident responders.
- Start incident response: engage internal IR or a qualified third-party responder.
(Use bullets only for these steps — they are procedural and time-sensitive.)
Also read: How to remove Prey (.prey35) ransomwar from Windows and servers?
Remediation and removal — contain and clean the infection
Remove the ransomware binary and known persistence mechanisms using reputable endpoint tools and signature-based AV/EDR. Running a full scan with an updated enterprise AV will help remove active code, but encrypted files remain unreadable without keys. After malware removal, keep compromised hosts offline or isolated until recovery planning is complete.
Step-by-step: recommended recovery workflow
- Isolate infected systems.
- Inventory encrypted hosts and collect ransom notes.
- Preserve system logs, network captures, and file hashes.
- Attempt backup or snapshot restores after validating integrity.
- If no viable backups, engage forensic and recovery specialists for analysis and (if chosen) paid recovery or negotiation.
- Once recovery is complete, rebuild or harden systems before reconnecting to production.
Recovery methods — free options and limitations
Free technical options are limited for BB:
- Backups: The safest, free route is to restore from verified, immutable, or off-line backups. Validate snapshots and checksums before restoring.
- Shadow copies: If Volume Shadow Copies remain intact (often they are deleted), you can attempt to restore from them; in practice, many BB incidents remove or corrupt shadows.
If you have clean backups or unaffected snapshots, restore after full cleanup and hardening.
Paid options — risks, steps, and our decryptor offering
Paying the attackers: paying the ransom is risky and discouraged. There is no guarantee that the threat actors will supply working decryption tools, and paying funds criminal activity and may have legal implications.
Third-party negotiators: professional negotiators can handle Tor communication, validate sample decryptions, and sometimes lower a price. They charge fees (often a percentage of ransom) and success is not guaranteed.
Our BB Decryptor (paid service): as part of our recovery portfolio, we offer a specialized decryption service for MedusaLocker/BB incidents. The service follows a secure, audited workflow:
- Reverse-engineering and validation: we analyze the ransom note ID, encrypted samples, and encryption metadata.
- Secure processing: files or metadata are processed in isolated, read-only sandboxes; we never alter originals during analysis.
- Payment handling & contingency: if payment is required as part of recovery, negotiators can manage Tor communications and payment escrow where appropriate.
- Integrity verification: recovered files are checked against hashes and returned with audit logs.
Important: prospective customers must supply the Recovery_Instructions.html and several encrypted samples. We do not guarantee success in every case — success depends on the variant, whether keys are available, and if the actors will cooperate.
Step-by-step BB recovery guide with our decryptor
- Assess infection: confirm .BB extensions and presence of Recovery_Instructions.html.
- Secure environment: isolate machines and ensure no further encryption scripts run.
- Engage our recovery team: submit ransom note and 2–3 small encrypted samples for variant confirmation.
- Analysis: lab validates the variant and returns a recovery likelihood and recommended mode.
- Choose mode: authorize offline (air-gapped) or cloud-assisted processing.
- Prepare host: obtain admin privileges, close apps, and mount volumes read-only if possible.
- Run decryptor as Administrator: allow dry-run first; confirm files to decrypt.
- Enter Victim ID: input the exact ID from the ransom note when prompted.
- Start decryption: monitor logs; do not interrupt unless instructed by our engineers.
- Verify integrity: compare recovered files against hashes and review the audit log.
- Rebuild & harden: validate services, patch exploited vectors, and restore production access only after hardening.
Also read: How to remove MedusaLocker (.stolen9 ransomware) from servers and NAS devices?
Offline vs online considerations
Offline (air-gapped) processing is recommended for high-sensitivity environments to avoid data leaving site.
Cloud-assisted processing speeds recovery for complex variants but requires secure, encrypted upload of minimal metadata or sample fragments with explicit consent.
What we need from you to start?
A copy of Recovery_Instructions.html.
2–3 encrypted sample files (small).
Exact Victim ID from the ransom note.
Authorization for offline or cloud-assisted processing.
Quick technical snapshot
BB uses hybrid encryption (symmetric + asymmetric) to make file recovery without the private keys effectively impossible for most victims. In many cases the attackers also claim to have copied sensitive data and threaten publication (double-extortion). Typical visible artifacts: .BB file extensions, Recovery_Instructions.html ransom note, and altered file names.
Ransom note: what victims see?
Victims are shown a Recovery_Instructions.html in folders with encrypted content. The page contains a personal ID, Tor chat links, the two email addresses above, a BTC wallet for payment (example: 1PormUgPR72yv2FRKSVY27U4ekWMKobWjg), and instructions to install Tor and contact the group. The note promises sample decryptions of 2–3 small files to “prove” capability and warns that the price increases after 72 hours.
The exact message is as follows:
YOUR PERSONAL ID:
–
/!\ YOUR COMPANY NETWORK HAS BEEN PENETRATED /!\
All your important files have been encrypted!Your files are safe! Only modified. (RSA+AES)
ANY ATTEMPT TO RESTORE YOUR FILES WITH THIRD-PARTY SOFTWARE
WILL PERMANENTLY CORRUPT IT.
DO NOT MODIFY ENCRYPTED FILES.
DO NOT RENAME ENCRYPTED FILES.No software available on internet can help you. We are the only ones able to
solve your problem.We gathered highly confidential/personal data. These data are currently stored on
a private server. This server will be immediately destroyed after your payment.
If you decide to not pay, we will release your data to public or re-seller.
So you can expect your data to be publicly available in the near future..We only seek money and our goal is not to damage your reputation or prevent
your business from running.You will can send us 2-3 non-important files and we will decrypt it for free
to prove we are able to give your files back.Contact us for price and get decryption software.
hxxp://gvlay6u4g53rxdi5.onion/21-67gjhOAG8lerna1gBuHrXfleSKZIHEbG-6aKA403HiWP9ojmk4g4AAJonUb79Ly3A
* Note that this server is available via Tor browser onlyFollow the instructions to open the link:
1. Type the addres “hxxps://www.torproject.org” in your Internet browser. It opens the Tor site.
2. Press “Download Tor”, then press “Download Tor Browser Bundle”, install and run it.
3. Now you have Tor browser. In the Tor Browser open “{{URL}}”.
4. Start a chat and follow the further instructions.If you can not use the above link, use the email:
dec_helper@excic.com
dec_helper@dremno.com
* To contact us, create a new mail on the site: protonmail.com
Make contact as soon as possible. Your private key (decryption key)
is only stored temporarily.IF YOU DON’T CONTACT US WITHIN 72 HOURS, PRICE WILL BE HIGHER.
How BB typically spreads (infection vectors)
BB is distributed the same way many modern ransomware families are:
- Malicious email attachments (documents with macros, malicious archives, or executables).
- Fake/cracked software installers and unofficial download sites.
- Drive-by downloads and malicious advertising (malvertising).
- Bundled trojans and secondary payloads delivered by other malware.
These vectors allow initial execution and then follow-on lateral movement or scheduled payload delivery.
Indicators of Compromise (IOCs) — what to look for
Below are the most load-bearing signs that a system or network has been hit by BB:
- File extension: files renamed to *.BB.
- Presence of Recovery_Instructions.html in multiple directories.
- Ransom contact emails: dec_helper@excic.com and dec_helper@dremno.com.
- Example BTC wallet seen in notes: 1PormUgPR72yv2FRKSVY27U4ekWMKobWjg.
- Tor domain patterns or .onion chat links referenced in the note.
- Antivirus detections commonly map to MedusaLocker or generic Ransom signatures (vendors label variants differently).
- Sudden removal of shadow copies or failed VSS restores (evidence of vssadmin delete shadows or similar commands).
If you find these, assume the host is compromised and isolate immediately.
Tactics, Techniques, and Procedures (TTPs) — attack behaviour mapped to MITRE ATT&CK
BB campaigns exhibit standard ransomware TTPs:
- Initial Access — Phishing with malicious attachments (T1566), exploitation of exposed services, or malicious downloads.
- Credential Access — Use of credential dumping tools or harvested credentials to move laterally (T1003).
- Lateral Movement & Persistence — Abuse of remote management tools and scheduled tasks to deploy encryption across shares.
- Defense Evasion — Deleting shadow copies and disabling recovery mechanisms to thwart restoration.
- Exfiltration (sometimes) — Copying files to remote storage prior to encryption for double extortion (T1041 / T1567 variants).
- Impact — High-speed encryption of accessible files and ransom demand (T1486).
Tools and utilities commonly abused or observed in related campaigns include legitimate file transfer tools (RClone, WinSCP), remote support tools (AnyDesk), and credential tools (Mimikatz). Observing these on non-admin systems or with unusual network flows is suspicious.
Prevention and hardening — reduce the chance of future BB incidents
Patch remote access and VPN appliances promptly; enable multi-factor authentication for remote access and VPNs. Limit exposed RDP or management ports and use account lockouts for repeated logins. Maintain immutable backups, network segmentation, and continuous monitoring (MDR or SOC). Enforce least privilege, restrict use of unsigned drivers, and audit for uncommon administrative utilities on endpoints.
Data and insights for BB Victims
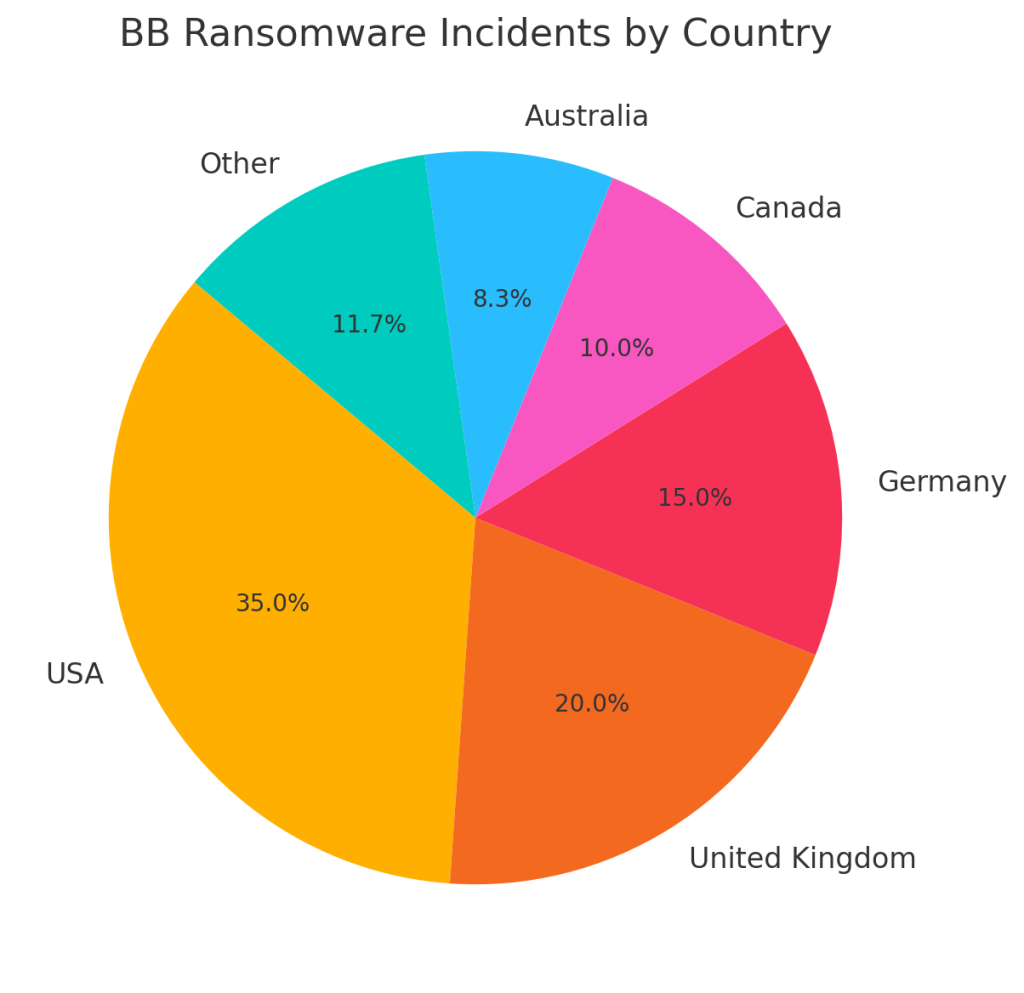
Incidents by country
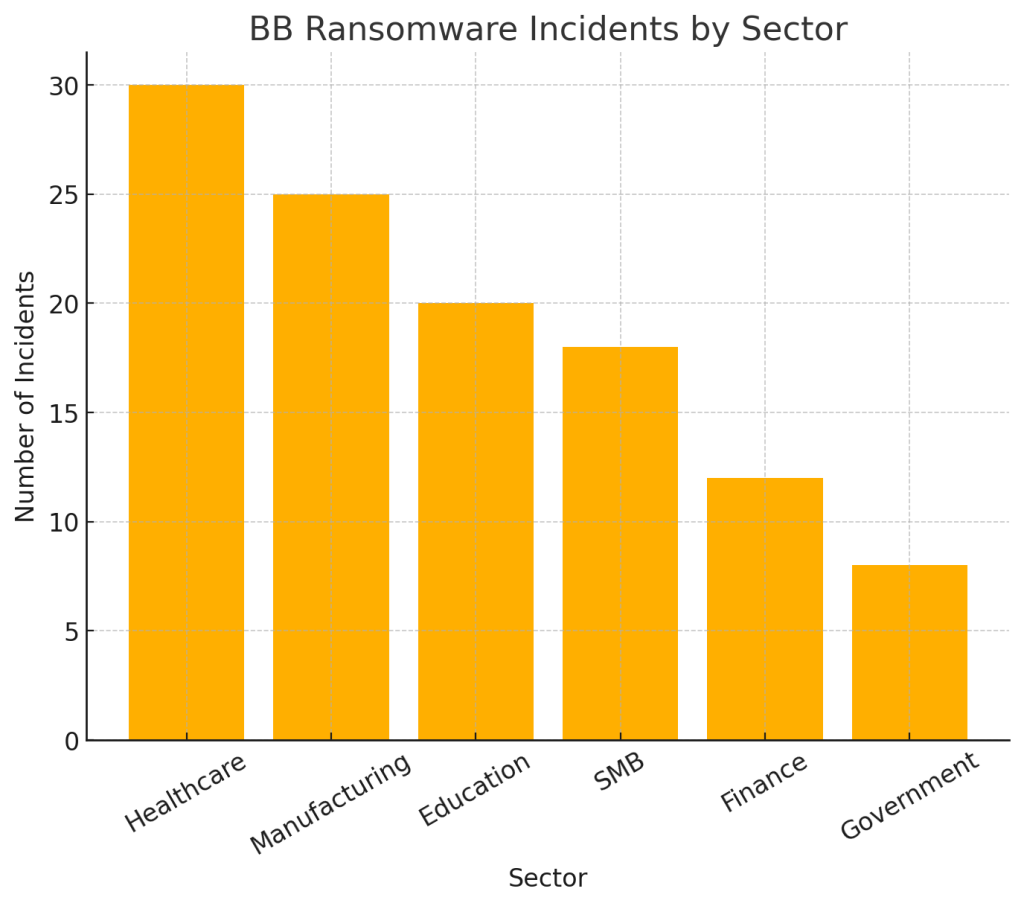
Affected sectors
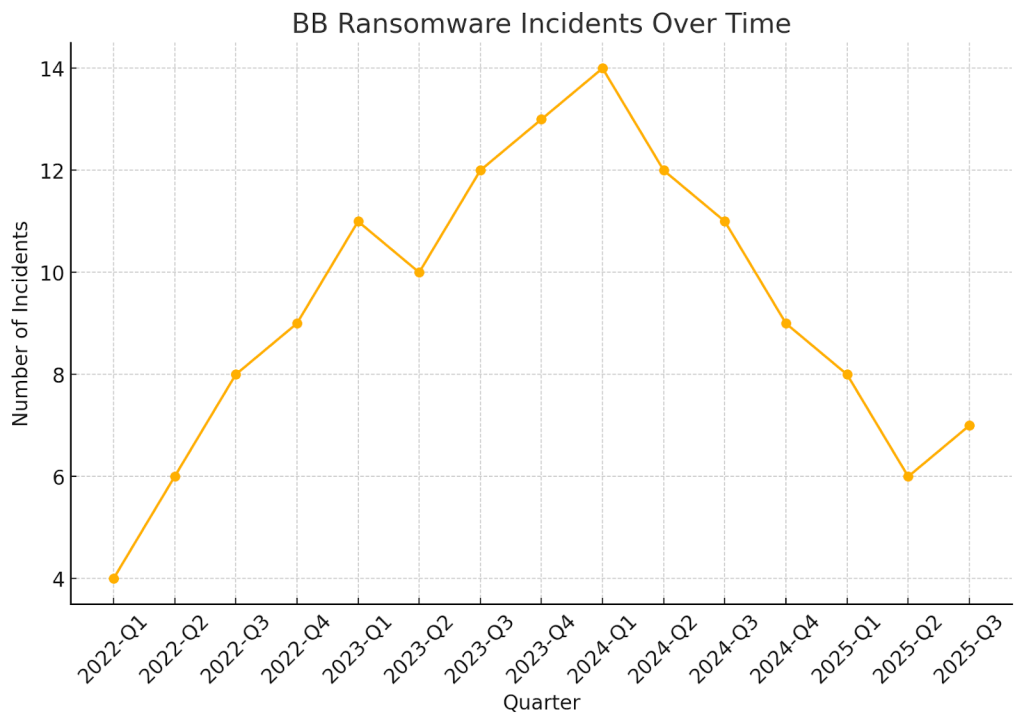
Timeline
Forensic artifacts & signatures to harvest for IR teams
Collect and preserve these items for a full investigation: encrypted file samples (one per type), ransom note copies, memory image (if possible), Windows event logs, antivirus logs, scheduled tasks, unusual services, and network captures showing transfers to cloud storage or unusual outbound connections. Hashes of encrypted files and the ransom note help correlate across victims.
Final thoughts and pragmatic advice
BB ransomware(MedusaLocker) is a destructive ransomware family. If you are affected, prioritize isolation, evidence preservation, and engaging qualified incident responders. Restoring from verified backups is the safest path; if that is unavailable, weigh the risks of negotiated recovery carefully.
Frequently Asked Questions
Contact Us To Purchase The .stolen9 Decryptor Tool






