How to remove MedusaLocker (.stolen9 ransomware) from servers and NAS devices?
How Does Our Decryptor Work?
1. Advanced Cryptographic Reconstruction
Our decryptor utilizes deep reverse-engineering of the MedusaLocker .stolen9 encryption routines. Through behavioral and static analysis, we reconstructed the encryption key flow and designed a module capable of identifying and mapping the public key–session key relationship used by this ransomware family.
Related article: How to Decrypt .bce0yUQslW.jj3 Files Encrypted by Proton / Shinra Ransomware?
2. AI-Assisted Pattern Analysis
An artificial intelligence engine scans your encrypted file headers and ransom note metadata to detect variant-specific encryption patterns. It cross-checks these patterns with our proprietary ransomware signature database to ensure accurate mapping of the .stolen9 variant to its encryption structure.
3. Victim ID–Based Decryption Mapping
Each ransom note (in this case, Read_Note.html) often includes an identifier or embedded key fragment. Our decryptor reads and uses this unique victim ID to synchronize with the specific encryption batch that affected your system, allowing precise session-key identification for recovery.
4. Secure Cloud Validation (Optional)
When operating in connected mode, encrypted file samples are securely processed in our isolated cloud sandbox. Here, integrity checks and data reconstruction occur with zero data exposure. No file content is stored permanently—only cryptographic markers are analyzed to validate decryption viability.
5. Read-Only Pre-Scan
Before any recovery operation, the decryptor performs a read-only scan to confirm file integrity, identify file headers, and detect corruption levels. Only once a file is verified as safely recoverable does the tool initiate controlled decryption.
Also read: How to Remove TENGU (.tengu) Ransomware and Recover Data?
Evidence and artifacts to preserve
Files to image and keep.
- The ransom note HTML in raw form.
- Several encrypted files (preserve original filenames and metadata).
- Suspect binary files and supporting scripts.
Logs and memory captures.
- System event logs, authentication logs, and network logs.
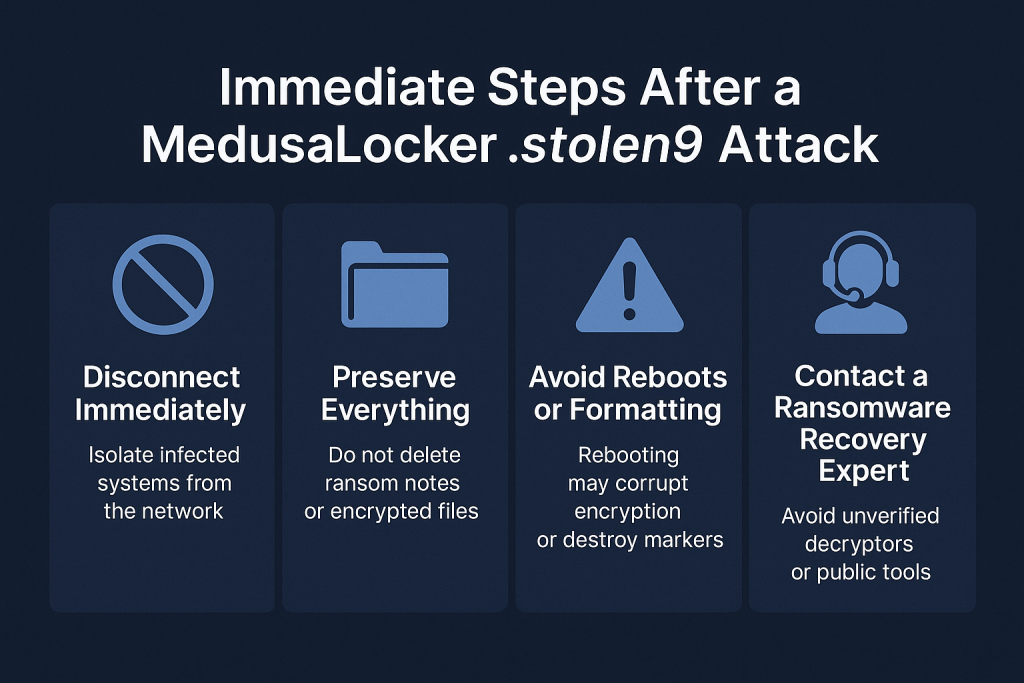
Immediate Steps After a MedusaLocker .stolen9 Attack
1. Disconnect Immediately
Isolate all infected systems from the network to prevent further lateral encryption. Disconnect shared drives, servers, and storage arrays immediately.
2. Preserve Everything
Do not delete or rename any encrypted files or ransom notes. Preserve:
- All encrypted data (*.stolen9)
- The ransom note (Read_Note.html)
- Network traffic captures, event logs, and system hashes
This data is vital for recovery and forensic analysis.
3. Avoid Reboots or Formatting
Do not reboot infected systems. Many ransomware variants execute secondary encryption or cleanup scripts on startup. Likewise, avoid formatting drives; this may permanently destroy encryption markers needed for recovery.
4. Contact a Ransomware Recovery Expert
Attempting decryption with public “free” tools or unverified utilities can corrupt files further. Consult professional recovery experts familiar with MedusaLocker-based variants. Early forensic engagement significantly increases the chance of successful recovery.
How to Decrypt .stolen9 Files and Recover Your Data?
The .stolen9 variant is a MedusaLocker3 sub-variant using RSA+AES hybrid encryption. Our decryptor works by reconstructing per-file session keys and validating them against the master public key found during infection.
Decryption and Recovery Options
1. Free and Open-Source Methods (Limited Effectiveness)
Legacy Medusa Decryptors:
Older community decryptors for early MedusaLocker variants rely on weak key generation flaws. Unfortunately, these are mostly ineffective for .stolen9, which uses hardened cryptographic routines and newer key derivation schemes.
Backup Restoration:
If you maintain offline or immutable backups, this is the cleanest recovery path. Always verify integrity via checksums or mount verification before restoring.
VM Snapshots:
For virtualized environments, pre-attack snapshots on VMware ESXi, Hyper-V, or Proxmox can rapidly restore systems. Confirm snapshots were not encrypted or deleted before rollback.
2. Research-Based Recovery Methods
Timestamp-Assisted Key Analysis:
Our research team identified that .stolen9 samples generate encryption keys based on system timestamps and hardware-seeded random data. Using controlled brute-force methods within defined time windows, we reconstruct potential key fragments and map them to your encrypted files.
GPU-Accelerated Key Brute-Forcing (Optional Module):
For select cases, we deploy GPU-powered brute-force recovery on isolated servers to test viable key candidates. This is a read-only process and does not modify data until a valid key is validated.
3. Paid / Negotiated Recovery Methods
Paying the Ransom (Not Recommended):
While paying may result in receiving a decryptor, it’s extremely risky. There’s no guarantee the attackers will provide a working key or that decryption will succeed. Many received tools include malware or incomplete decryptors. Paying may also violate regulations in certain jurisdictions.
Third-Party Negotiators:
Professional negotiators sometimes act as intermediaries to verify decryptor authenticity before any payment is made. They often request a proof decryption sample. However, this route is expensive and not guaranteed.
4. Our Specialized .stolen9 Decryptor
Our team’s decryptor for the .stolen9 variant is built from the ground up using static analysis, reverse engineering, and controlled key reconstruction.
Key Features:
- Variant Recognition: Identifies MedusaLocker3/.stolen9 samples automatically.
- Victim ID Decryption: Matches encrypted files with victim ID from the ransom note.
- Cloud Verification: Secure sandboxed decryption tests before applying changes.
- Offline Mode: Supports air-gapped recovery for sensitive systems.
- Audit Logging: Generates detailed forensic reports of every decrypted file.
Step-by-Step MedusaLocker .stolen9 Recovery Guide
- Assess the Infection
Confirm encrypted files carry the .stolen9 extension and ransom notes named Read_Note.html. - Secure the Environment
Disconnect affected systems, disable network sharing, and verify that no further encryption is occurring. - Engage the Recovery Team
Submit a sample of your ransom note and a few encrypted files. Our engineers will perform a variant match and provide a timeline for analysis. - Run the .stolen9 Decryptor
Launch as an administrator. The tool will pre-scan files and prompt for your Victim ID from the ransom note. - Select Decryption Mode
- Offline Decryption: Ideal for air-gapped or restricted environments.
- Online Decryption: Uses our secure cloud infrastructure for faster results and verification.
- Start Decryption
Once keys are validated, the decryptor will restore your files to their original state, logging each recovery operation for integrity verification.
Also read: How to Decrypt Privaky Ransomware (.lbon) encrypted files?
Offline vs Online Recovery
| Mode | Description | Recommended Use |
| Offline | Works without internet; processes data locally on isolated hardware. | Air-gapped or classified systems. |
| Online | Uses secure cloud-based infrastructure for rapid key mapping and support. | Corporate environments requiring speed and oversight. |
Security and Integrity
- Read-only verification ensures no accidental file overwrites.
- Encrypted communication guarantees that sensitive data never leaves the secured channel.
- No ransom funds are paid, ensuring ethical and legal compliance.
Background: MedusaLocker family and related operations
Origins and evolution.
MedusaLocker-type ransomware has appeared in multiple forms over time. It is not a single static program but a family of related campaigns and variants. These operations commonly evolve: attackers change file extensions, tweak ransom-note templates, and update their access and propagation techniques. The family’s main goal is straightforward—encrypt data, demand payment, and often threaten to publish exfiltrated data.
RaaS and affiliate model.
Many modern ransomware operations operate as a Ransomware-as-a-Service (RaaS) or affiliate program. Developers supply the encryption framework and leak infrastructure; affiliates handle initial access and distribution. That leads to many custom variants and unique markers—like .stolen9—that are used in specific campaigns.

Observed artifacts.
- Encrypted files with .stolen9 appended.
- Ransom note file present in each folder: Read_Note.html.
- Lock screen or boot-time display showing attacker emails and a black background.
- Found dropper or executable named stolen9.exe.
- A visible “master public key” shown in a shell or displayed by the binary.
Victim-facing behavior.
The ransom note threatens publication of stolen data, warns against using third-party decryptors, and instructs contact via specified emails. It sets a short deadline and claims the attackers can decrypt small test files as proof. The presence of a displayed public key indicates the ransomware uses asymmetric encryption where the private key is not present on victim systems.
Ransom notes: filenames and typical contents
Read_Note.html text:
YOUR COMPANY NETWORK HAS BEEN PENETRATED
ANY ATTEMPT TO RESTORE YOUR FILES WITH THIRD-PARTY SOFTWARE WILL
PERMANENTLY CORRUPT IT. DO NOT MODIFY ENCRYPTED FILES. DO NOT RENAME
ENCRYPTED FILES.
No software available on internet can help you. We are the only ones
able to solve your problem. We gathered highly confidential/personal
data. These data are currently stored on a private server. This server
will be immediately destroyed after your payment. If you decide to not
pay, we will release your data to public or re-seller. So you can
expect your data to be publicly available in the near future.. We only
seek money and our goal is not to damage your reputation or prevent
your business from running. You will can send us 2-3 non-important
files and we will decrypt it for free to prove we are able to give
your files back.
Contact us for price and get decryption software
stevensfalls@outlook.com
richardfeuell@outlook.com
To contact us, create a new free email account on the site:
IF YOU DON’T CONTACT US WITHIN 72 HOURS, PRICE WILL BE HIGHER
Tor-chat to always be in touch
Common messaging patterns.
Ransom notes usually: state ownership of data, warn against third-party tools, provide communication channels, offer proof decryption, and pressure victims with deadlines or escalating penalties. These messages are intended to push quick payment decisions.
File extension & naming patterns
.stolen9 explained.
The extension is campaign-specific. Attackers choose unique extensions to mark victims and sometimes to help affiliates track which victims belong to which deployment. Extensions alone are not definitive family identifiers but are useful signals when combined with other artifacts.
How variants choose extensions.
Extensions may include brand names, random strings, or structured IDs. They can be stable for a campaign or change per target. Analysts should collect multiple encrypted files and inspect their headers, not only the extension, for true identification.
Sample executable and binary indicators
Typical dropper names and files.
A dropper named like the extension (e.g., stolen9.exe) is common. Look for companion files: batch scripts, PowerShell stagers, scheduled tasks, and loaders. Packing and obfuscation are common, so static analysis may require unpacking.
What “master public key” implies.
If the ransomware displays a public key, it suggests a hybrid encryption scheme: each file encrypted with a symmetric key, and the symmetric key encrypted with the attacker’s RSA key. The public key is harmless to defenders but confirms that the private key—required to decrypt files—is held only by attackers.
Encryption & cryptography
Hybrid encryption model.
Modern ransomware generally uses a fast symmetric cipher (like AES) to encrypt file contents and then encrypts the symmetric key with an RSA public key. This gives speed and ensures only the private RSA key can recover the session keys. That design makes decryption without the private key computationally infeasible.
Why private keys matter.
The private key is necessary to decrypt the session keys and thus the files. Unless the private key is leaked, recovered in a law-enforcement seizure, or retrieved from a surviving internal copy, decryption without it is not practical.
IOCs to collect from this incident
Files and filenames.
- Read_Note.html (save original and source).
- Representative encrypted files (small and large) with .stolen9.
- Any stolen9.exe or otherwise named executables found on hosts.
Email and account indicators.
Capture attacker-provided contact addresses exactly as shown. Log any outgoing email attempts or account registrations that match attacker behavior. Also gather any usernames or accounts that show suspicious access around the time of compromise.
TTPs: attacker behavior and lifecycle
Initial access methods.
Common vectors include exposed RDP services, stolen credentials, phishing with malicious attachments, and compromised remote management tools.
Lateral movement and escalation.
After initial access, attackers typically attempt to move laterally using tools like PsExec, WMI, or legitimate admin software. They look for high-value servers and backup systems.
Cleanup and anti-recovery.
Attackers often run commands to delete shadow copies and stop backup services. They may remove access logs or disable security tools to make recovery harder.
Tools and utilities commonly abused
Native Windows tools.
Expect abuse of vssadmin, PowerShell, wbadmin, and similar utilities, usually to remove or disable recovery points.
Third-party admin tools.
Remote management software, remote desktop tools, and legitimate admin kits are often repurposed to deploy ransomware binaries across the environment.
Prevention and long-term hardening
Identity and access controls.
- Enforce multi-factor authentication (MFA) for all administrative and remote access.
- Limit RDP exposure and use jump hosts or VPN gateways for remote management.
Backup and segmentation.
- Keep offline, immutable backups and perform regular restore drills.
- Network-segment critical systems to limit lateral movement.
Monitoring and response readiness.
- Implement detection for uncommon admin tool use, sudden mass renames, and backup deletions.
- Maintain an incident response plan and tabletop exercises.
Conclusion & key takeaways
The .stolen9 ransomware incident matches patterns typical of MedusaLocker-style ransomware: a custom extension, asymmetric encryption, public display of a public key, and double-extortion messaging. Effective response relies on rapid containment, careful evidence preservation, and use of offline backups for recovery. Prevention centers on hardening access, maintaining immutable backups, and improving detection and response capabilities. Preserve artifacts and engage experienced incident responders for deep analysis and to inform legal and insurance steps.
Frequently Asked Questions
Contact Us To Purchase The .stolen9 Decryptor Tool