How to Remove TENGU (.tengu) Ransomware and Recover Data?
Our TENGU Decryptor: Rapid Recovery, Expert-Engineered
At this time there is no publicly verified decryptor for TENGU. Our focus is rapid containment, clean restoration, and forensics-led recovery that preserves evidence, minimizes downtime, and meets regulatory needs. We combine incident response, snapshot restoration, and safe data handling aligned to trusted guidance.
Related article: How to Decrypt Privaky Ransomware (.lbon) encrypted files?
How It Works?
- Forensic triage first: Memory, logs, ransom artifacts, network traces—collected before any reboot.
- Scope & isolate: Identify affected hosts/shares; segment and block malicious egress.
- Clean restore: Leverage immutable/offline backups and snapshots; validate integrity before cut-over.
- Targeted hunts: Behavior-based detections for mass file renames, shadow-copy deletion, and Tor/tunneling traffic.
- Governance & reporting: Support for legal, compliance, and notifications guided by recognized best practices.
Also read: How to Decrypt Wiper Ransomware (.ahG5ooth) files safely?
Requirements
- Access to encrypted files and any ransom note(s) found on hosts or shares.
- Administrative privileges (local/domain) during the recovery window.
- Network and endpoint logs (Windows Event, Sysmon/EDR, VPN/firewall).
- Backups or VM snapshots (ideally immutable or offline).
- Connectivity for remote IR (optional) and to reach validated guidance (e.g., CISA).
Immediate Steps to Take After TENGU Ransomware Attack
- Disconnect & isolate affected systems; don’t power them off before memory capture.
- Preserve everything: ransom notes, encrypted samples, logs, PCAPs, EDR exports.
- Block outward comms: especially to Tor gateways/tunnels and unknown TLS endpoints.
- Secure credentials: disable suspected accounts, rotate privileged creds, revoke tokens.
- Engage IR expertise and review the CISA Ransomware Response Checklist.
How to Decrypt TENGU Ransomware and Recover Your Data?
- Primary path: restore from clean, verified backups/snapshots after eradication.
- No public decryptor: avoid unverified tools; they risk corruption and reinfection.
- Test restores in isolation: mount snapshots read-only; checksum and spot-check critical apps.
- Document chain-of-custody for all artifacts to support insurance and legal needs.
TENGU Decryption and Recovery Options
Free Methods
1. Backup Restore
- Isolated recovery: wipe/reimage and restore to known-good baselines.
- Integrity checks: verify snapshots with checksums before cut-over.
- Immutable advantage: WORM/cloud immutability greatly improves resilience.
2. VM Snapshots
- Rollback from pre-attack state where snapshots exist and are intact.
- Snapshot hygiene: ensure attackers didn’t delete or tamper with hypervisor snapshots; validate logs first.
Researcher/Academic Tools
No vetted researcher tools (GPU/brute-force) exist for TENGU at this time. Keep focus on hygiene, backups, and eradication.
Paid Methods
Paying the Ransom
- Not recommended: no guarantee of working keys; may introduce additional malware and legal/ethical issues.
- If considered: consult counsel, insurer, and qualified negotiators; demand proof (test decryption) before any step.
Third-Party Negotiators
- Can validate threat-actor claims and reduce risk, but fees and outcomes vary. Keep regulators and legal informed as required.
Our Specialized TENGU Ransomware Recovery
How It Works?
- Evidence preservation & scope (hosts, shares, identity, egress).
- Eradication & hardening (kill persistence, rotate creds, patch).
- Restoration (immutable backups/snapshots), validation, and business cut-over.
- Lessons learned and control upgrades to resist future intrusions
Step-by-Step TENGU Recovery Guide with TENGU Playbook
- Assess the Infection
- Identify widespread file renames and ransom notes; check for .tengu-suffixed files on shares.
- Secure the Environment
- Segment affected VLANs; block suspicious outbound traffic (Tor/tunnels).
- Segment affected VLANs; block suspicious outbound traffic (Tor/tunnels).
- Forensic Collection
- Collect memory, event logs, Sysmon/EDR, and the ransom note(s).
- Eradicate & Patch
- Remove persistence, update appliances, enforce MFA, and close exposed services.
- Restore Carefully
- Use offline/immutable backups or clean snapshots; verify before production.
- Validate & Monitor
- Watch for re-encryption, lateral movement, or data-exfil retries.
Also read: How to Decrypt .386355D7 Files After C77L / Nullhexxx Ransomware Attack?
Offline vs Online Decryption Methods
- Offline (air-gapped): safest for sensitive estates; use external media and secured jump hosts.
- Online (assisted): faster when working with trusted IR teams, secure transfer, and auditable workflows
Our recovery supports both modes — enterprise to SMB
We can operate fully offline in air-gapped environments or in secured online engagements with evidence logging, change control, and executive reporting.
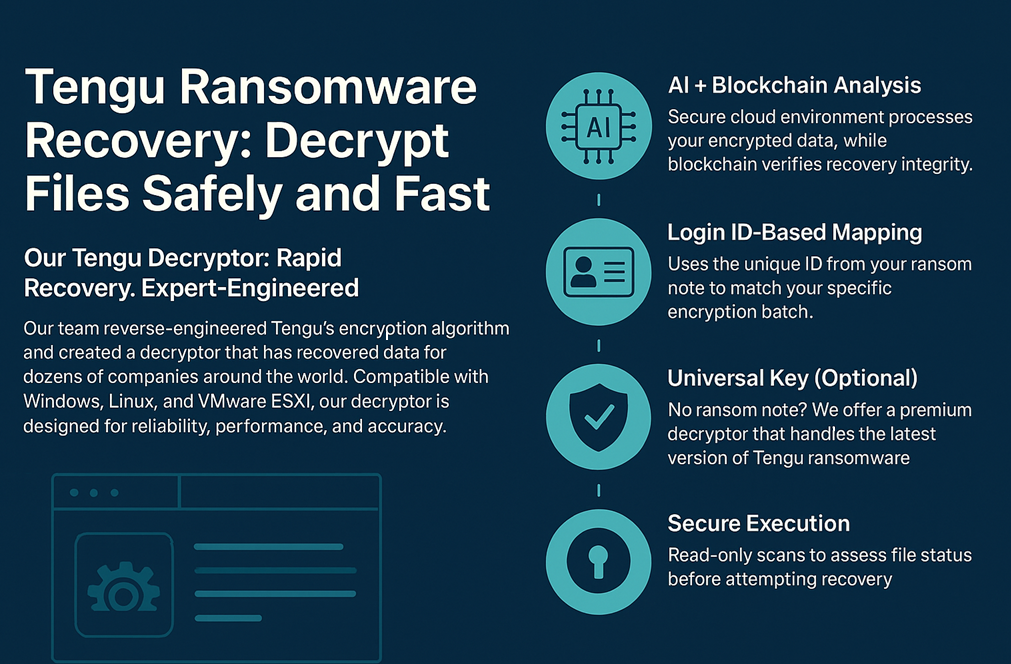
What is TENGU Ransomware?
TENGU is a newly observed ransomware/leak operation with a public onion presence and a tracker profile created October 10, 2025. As with other double-extortion groups, organizations should assume data theft attempts may precede any encryption event.
Lineage & Affiliations
There is no confirmed technical lineage publicly documented for TENGU yet (e.g., code overlap or shared actors). Trackers list the group and its infrastructure; keep monitoring threat-intel updates for any future ties.
How TENGU Works: The Inside Look
Initial Access Vectors: How TENGU Gets In
- Exposed remote access: weak/no MFA on VPN/RDP.
- Phishing & credential theft.
- Exploited appliances/services: unpatched internet-facing devices. (Follow CISA mitigations.)
Tools, TTPs & MITRE ATT&CK Mapping (what to hunt)
- Credential Access: LSASS dumping, password reuse (ATT&CK T1003, T1555).
- Discovery/Lateral Movement: LDAP/AD queries, RDP/PSExec/WMI (T1018, T1021).
- Defense Evasion: LOLBins (powershell, rundll32), AV tampering (T1218, T1562).
- Exfiltration: cloud drives (Rclone/Mega), SFTP, web services (T1041, T1567).
- Impact: file encryption and shadow copy deletion (vssadmin) (T1486). See CISA StopRansomware Guide for detailed mitigations.
Known TENGU Indicators of Compromise (IOCs)
- Leak/Media Site: TENGU entry on RansomLook (first published 2025-10-10).
- Onion Address (reported): fuvodyoktsjdwu3mrbbrmdsmtblkxau6l7r5dygfwgzhf36mabjtcjad[.]onion (defang in enterprise tooling if required).
Continue to collect: ransom notes, encrypted filenames (look for .tengu), hashes of suspicious binaries, and any outbound endpoints seen during the event.
Mitigations and Best Practices
- MFA everywhere (VPN, admin, remote access).
- Patch fast for internet-facing systems; prioritize appliance CVEs.
- Disable internet-facing RDP; restrict by VPN + MFA if required.
- Network segmentation and tiered admin workstations.
- Immutable/offline backups with routine restore tests.
- EDR with behavioral rules; log centralization (Sysmon/Windows Events).
- CISA StopRansomware: use the checklist and hardening guidance
Statistics and Facts So Far Regarding TENGU Ransomware
- First public listing: Oct 10, 2025 (RansomLook group entry).
- Public presence: onion address mentioned by threat-intel monitors.
- Victim disclosures: none formally published on the tracker page at time of writing.
Ransom Note Dissected: What They Say and Why
If you find a note (README/HTML/HTA) alongside encrypted files:
- Extract the victim ID, contact method (often Tor), and any payment instructions.
- Save notes verbatim; don’t edit or re-save to different encodings.
- Provide the note to incident responders for cross-reference with the leak site and tracker posts. (Trackers: RansomLook, general guidance: CISA.
Conclusion: Restore Your Data, Reclaim Your Network
TENGU ransomware is now on the radar, with a tracker profile and onion presence. Treat events decisively: isolate, preserve, hunt, eradicate, and restore clean. Keep your controls aligned to CISA StopRansomware and monitor for newly published TENGU artifacts (hashes, notes, samples).
Frequently Asked Questions
Contact Us To Purchase The TENGU Decryptor Tool