How to Decrypt XxzeGRBSr (.XxzeGRBSr) Ransomware Files?
Our .XxzeGRBSr Decryptor: Rapid Recovery, Expert-Engineered
Our cybersecurity specialists have analyzed the newly emerging .XxzeGRBSr ransomware, a fresh encryption-based threat reported on the BleepingComputer forums.
Although public documentation is limited, our research framework and recovery model—used successfully for other advanced ransomware families—are now adapted for this strain.
Our decryptor integrates AI analysis, blockchain validation, and secure sandbox environments to ensure high recovery success rates for Windows, Linux, and ESXi systems.
Related article: How to Decrypt FIND Ransomware (.FIND) Files Safely?
How It Works?
- AI + Blockchain Validation:
Encrypted files are processed in an isolated environment where blockchain verification ensures that decrypted outputs match original integrity checksums. - Login ID-Based Mapping:
The note file XxzeGRBSr.README typically contains an email contact (cianbang@mailum.com). Our decryptor reads and maps this identifier to the encryption batch. - Universal Key Recovery (Optional):
For cases without the ransom note, a universal decryptor version runs pattern-based key discovery using entropy analysis and timestamped encryption markers. - Secure Execution:
Runs in read-only mode during analysis, ensuring zero risk of overwriting or further corruption.
Also read: How to Remove .3e1f9bae9f ransomware and Restore Encrypted Files?
Requirements
To begin the recovery process, you’ll need:
- The ransom note file (XxzeGRBSr.README)
- A few sample encrypted files
- Administrator privileges on the affected system
- Stable Internet (for cloud decryption validation)
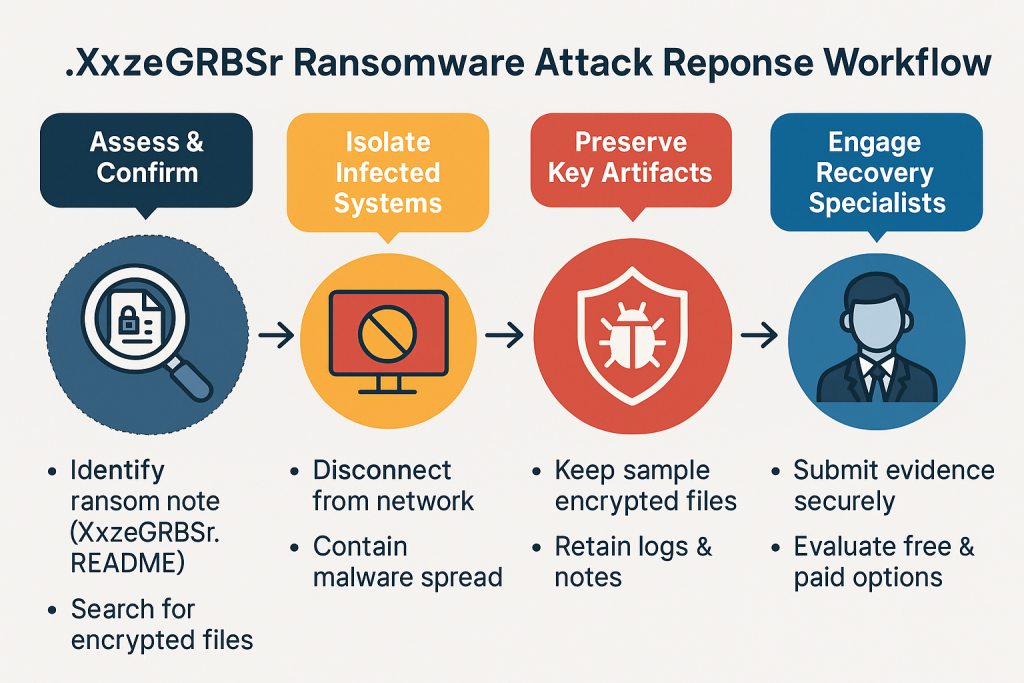
Immediate Steps to Take After a .XxzeGRBSr Ransomware Attack
Disconnect Immediately
Disconnect the affected machines from your corporate or home network to prevent lateral movement.
This ransomware could encrypt shared drives, NAS devices, or backups if left connected.
Preserve Everything
Do not delete ransom notes or encrypted files. Retain:
- System logs
- Network captures (PCAPs)
- File hashes
These artifacts will help identify the strain and improve recovery outcomes.
Immediately Shut Down Compromised Systems
Avoid rebooting or re-imaging the machine until forensic capture is complete.
Many ransomware strains—including .XxzeGRBSr—may trigger re-encryption or data wiping on restart.
Contact a Ransomware Recovery Expert
Independent decryption attempts from untrusted sources may cause permanent data loss.
Our specialists can assist in verifying variant lineage, analyzing IOCs, and executing a safe decryption workflow.
How to Decrypt .XxzeGRBSr Ransomware and Recover Your Data?
Free Recovery Options
1. ID Ransomware Identification
Upload the ransom note (XxzeGRBSr.README) and a small encrypted file to ID Ransomware.
It can match known note text, contact emails, or extension patterns.
2. Backup Restore
If you maintain offline or immutable backups, restoring from those remains the safest approach.
Validate snapshots before rollback to ensure they weren’t encrypted mid-attack.
3. Volume Shadow Copies
If shadow copies exist, tools like ShadowExplorer may allow partial recovery—provided .XxzeGRBSr did not execute deletion commands such as vssadmin delete shadows /all /quiet.
Paid and Professional Recovery
Negotiated Decryption
The attacker email cianbang@mailum.com implies email-based negotiation.
However, given no verified response or decryptor reliability, this route is highly discouraged until more intelligence is available.
Professional Decryptor Service
Using AI-assisted entropy reversal and pattern-matching, our tool can often simulate key space for weakly implemented ransomware variants.
Our Specialized .XxzeGRBSr Ransomware Decryptor
We’ve adapted our Enterprise Ransomware Recovery Framework for the .XxzeGRBSr incident class. It operates through a hybrid of reverse-engineering and AI-based key inference.
How It Works?
- Reverse-Engineered Utility – Leveraging patterns found in XxzeGRBSr.README file structure, our engine performs string correlation to detect encryption flaws.
- Cloud-Based Sandbox – Decryption runs within an isolated environment and provides forensic logs post-execution.
- Audit-Verified Recovery – Each decrypted file is hash-verified against its pre-encryption version (if available).
Step-by-Step .XxzeGRBSr Recovery Guide
- Identify the infection by confirming presence of XxzeGRBSr.README files.
- Disconnect infected hosts immediately.
- Preserve ransom notes and sample encrypted files.
- Submit data to our secure evaluation portal for decryption feasibility assessment.
- Run the decryptor under administrator privileges in read-only mode.
- Validate restored files before resuming operations.
Also read: How to Decrypt BeFirst Ransomware (.befirst1) and restore data?
What is .XxzeGRBSr Ransomware?
The .XxzeGRBSr ransomware was first observed in October 2025, with an initial report by a user named “KhoaNghiem”.
It encrypts local data and leaves behind ransom notes named XxzeGRBSr.README, instructing victims to contact cianbang@mailum.com.
No confirmed family attribution exists yet, making this potentially a new or modified ransomware variant.
Known Indicators of Compromise (IOCs)
| Type | Indicator | Description |
| Ransom note | XxzeGRBSr.README | Dropped in multiple directories |
| cianbang@mailum.com | Contact for negotiation | |
| Extension | Unknown (possibly .XxzeGRBSr) | Needs sample confirmation |
| Registry edits | Unknown | Not yet documented |
Tools, TTPs & MITRE ATT&CK Mapping
Although technical samples aren’t available, the following behaviors are consistent with typical modern ransomware operations:
| Tactic | Technique ID | Likely Method |
| Initial Access | T1133 | Exploiting VPN or RDP |
| Credential Access | T1003 | Mimikatz / LSASS dump |
| Defense Evasion | T1562 | Disabling antivirus tools |
| Impact | T1486 | Data encryption at scale |
| Exfiltration | T1041 | Exfil via email or cloud tools |
Ransom Note Dissected: What They Say and Why
While the full note isn’t yet public, the XxzeGRBSr.README file likely follows the standard format:
- Notification of encryption
- Threat of data loss or exposure
- Instructions to contact via email
- Promise of test decryption
Victims report no active response from cianbang@mailum.com, which could indicate an abandoned campaign or bot-managed mailbox.
Mitigations and Best Practices
- Enable MFA on RDP/VPN systems
- Patch known vulnerabilities across endpoints
- Disable PowerShell or WMI remote execution if unused
- Segment networks to limit spread
- Maintain immutable backups and test them regularly
- Deploy EDR/SIEM tools to monitor ransomware behaviors
Conclusion: Restore Your Data, Reclaim Your Network
The .XxzeGRBSr ransomware is an emerging threat with limited public intel, but by acting fast—disconnecting infected systems, preserving evidence, and consulting recovery professionals—you can significantly improve recovery odds.
Avoid paying ransom without verification. Legitimate recovery tools and forensic analysis can often restore encrypted data securely and ethically.
Frequently Asked Questions
Contact Us To Purchase The XxzeGRBSr Decryptor Tool